
《King of the Hill》(KoTH)是一款竞争性黑客游戏,在游戏中你要与 10 名黑客对抗,攻破一台机器,然后修补其漏洞,阻止其他玩家获得访问权限。你保持访问的时间越长,你得到的积分就越多。
账号设置
注册完之后加入不了房间,提示 Uh-oh! Only intermediate and advanced experienced leveled users can play King of the Hill.

《King of the Hill》(KoTH)是一款竞争性黑客游戏,在游戏中你要与 10 名黑客对抗,攻破一台机器,然后修补其漏洞,阻止其他玩家获得访问权限。你保持访问的时间越长,你得到的积分就越多。
注册完之后加入不了房间,提示 Uh-oh! Only intermediate and advanced experienced leveled users can play King of the Hill.
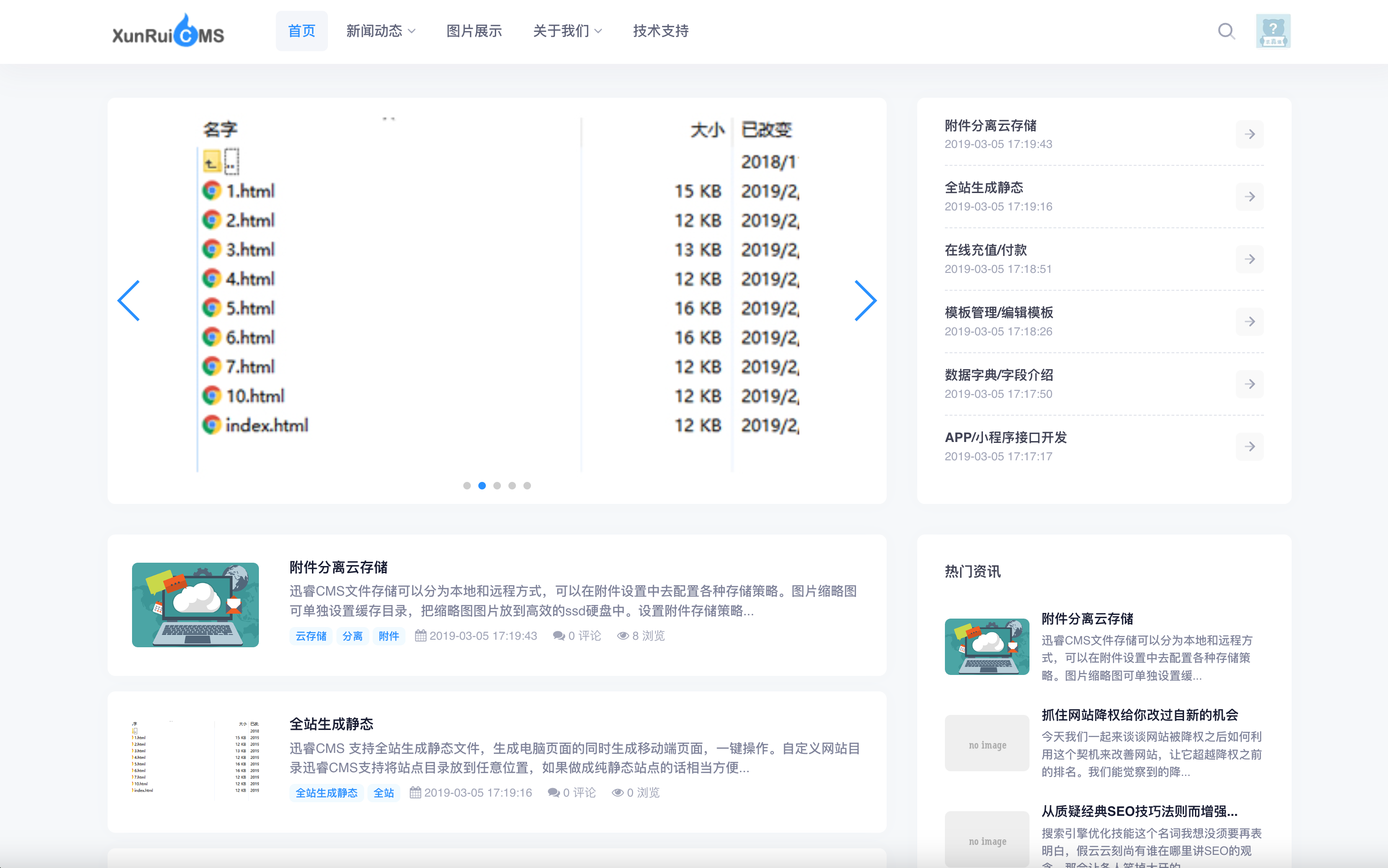
简单的 cms,可以扫扫看?
提示 1: /flag.php:
if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){
echo "Just input 'cmd' From 127.0.0.1";
return;
}else{
system($\_GET['cmd']);
}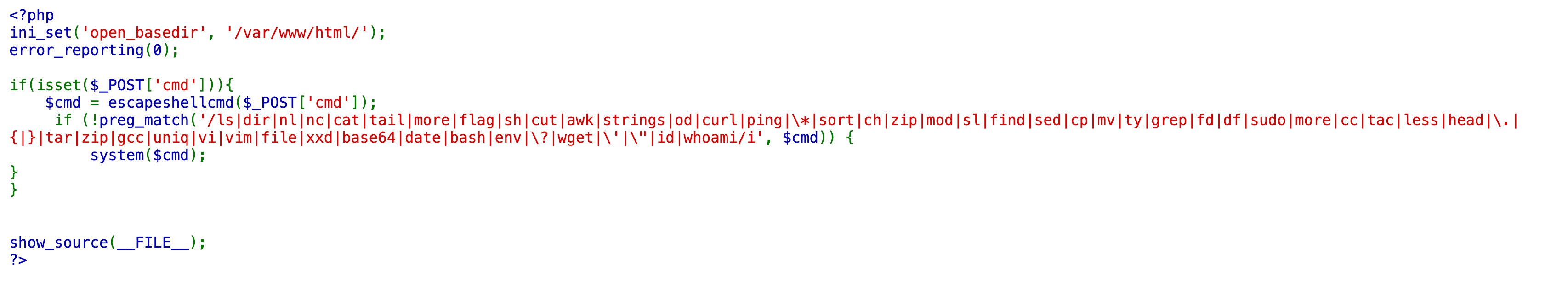
小明在学习 CTF 的过程中遇到了一道 PHP 的题目,以他有限的水平做不出来,可以帮帮他吗?
观察源码,只要我们传进去的 cmd 不被正则匹配到,就可以执行系统命令。
if(isset($_POST['cmd'])){
$cmd = escapeshellcmd($_POST['cmd']);
if (!preg_match('/ls|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\*|sort|ch|zip|mod|sl|find|sed|cp|mv|ty|grep|fd|df|sudo|more|cc|tac|less|head|\.|{|}|tar|zip|gcc|uniq|vi|vim|file|xxd|base64|date|bash|env|\?|wget|\'|\"|id|whoami/i', $cmd)) {
system($cmd);
}
}
Someone said: 'One advantage of having a homemade server is that it becomes much harder to hack.' Do you agree? Give reasons.
Note: The files in src/public are unrelated for the challenge.
Chilli Level:
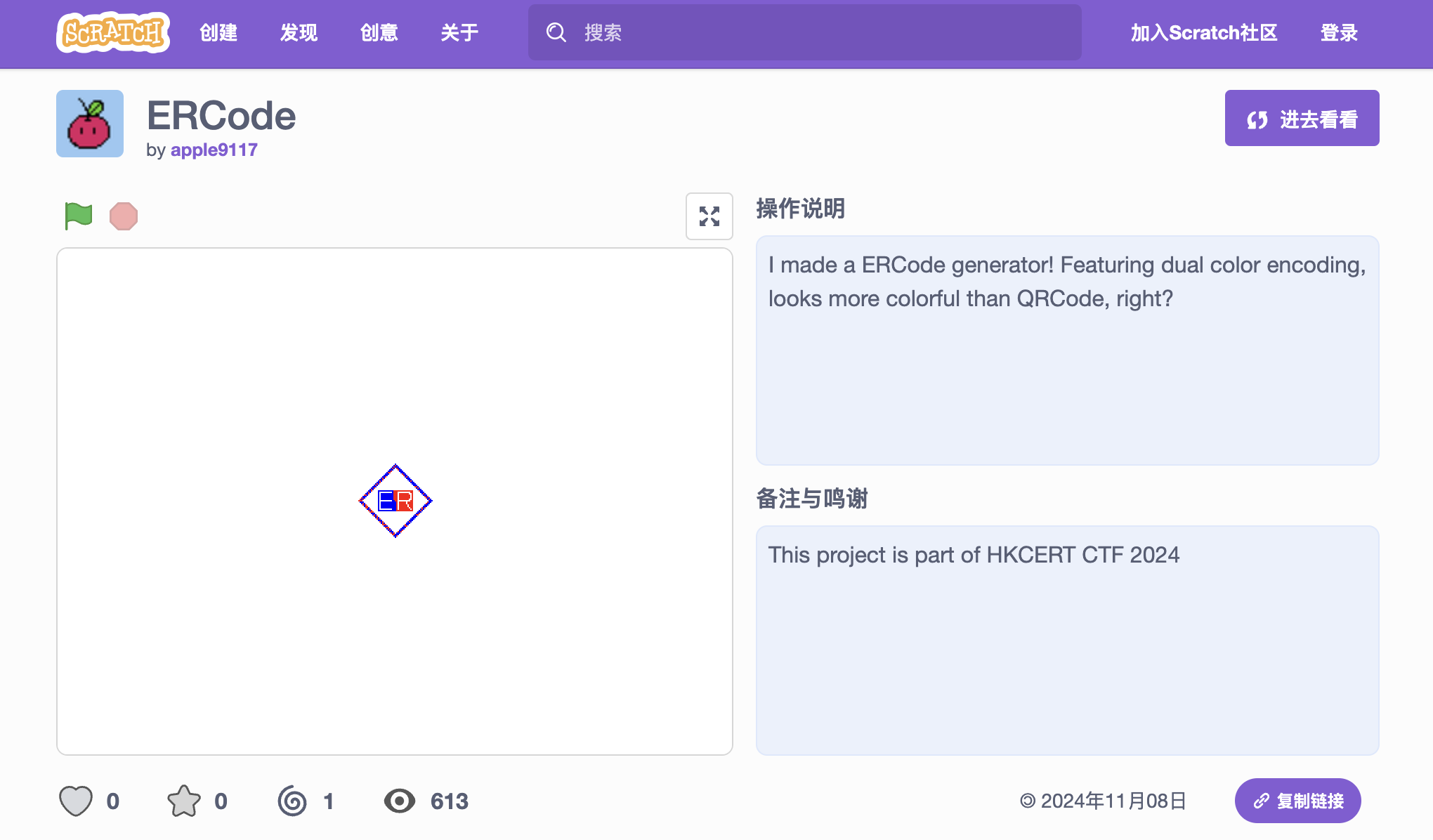
I made a ERCode generator! Featuring red-blue encoding, looks more colorful than QRCode, right?
Flag is in the ERCodes.

"A QA engineer walks into a bar. Orders a beer. Orders 0 beers. Orders 99999999999 beers. Orders a lizard. Orders -1 beers. Orders a ueicbksjdhd."
I am working on yet another CTF platform. I haven't implement all the features yet, but I am confident that it is at least secure.
Thanks to Poe I coded a webpage to PDF in seconds! I am genius right?
Chilli Level:
该网站是一个可以发布帖子的网站,同时可以上传图片,所以在源码中关注一下图片上传的地方有没有漏洞
观察源码我们可以发现,这里对每张上传的图片都用 convert 函数进行了处理
router.post(
"/post",
AuthRequired,
fileUpload({
limits: {
fileSize: 2 * 1024 * 1024,
},
}),
ValidationMiddleware("post", "/forum"),
async function (req, res) {
const { title, message, parentId, ...convertParams } = req.body;
if (parentId) {
const parentPost = await db.getPost(parentId);
if (!parentPost) {
req.flashError("That post doesn't seem to exist.");
return res.redirect("/forum");
}
}
let attachedImage = null;
if (req.files && req.files.image) {
const fileName = randomBytes(16).toString("hex");
const filePath = path.join(__dirname, "..", "uploads", fileName);
try {
const processedImage = await convert({
...convertParams,
srcData: req.files.image.data,
format: "AVIF",
});
await fs.writeFile(filePath, processedImage);
attachedImage = `/uploads/${fileName}`;
} catch (error) {
req.flashError(
"There was an issue processing your image, please try again."
);
console.error("Error occured while processing image:", error);
return res.redirect("/forum");
}
}
const { lastID: postId } = await db.createPost(
req.session.userId,
parentId,
title,
message,
attachedImage
);
if (parentId) {
return res.redirect(`/forum/post/${parentId}#post-${postId}`);
} else {
return res.redirect(`/forum/post/${postId}`);
}
}
);
拿到一个 .bin 文件,使用 binwalk 解压此固件
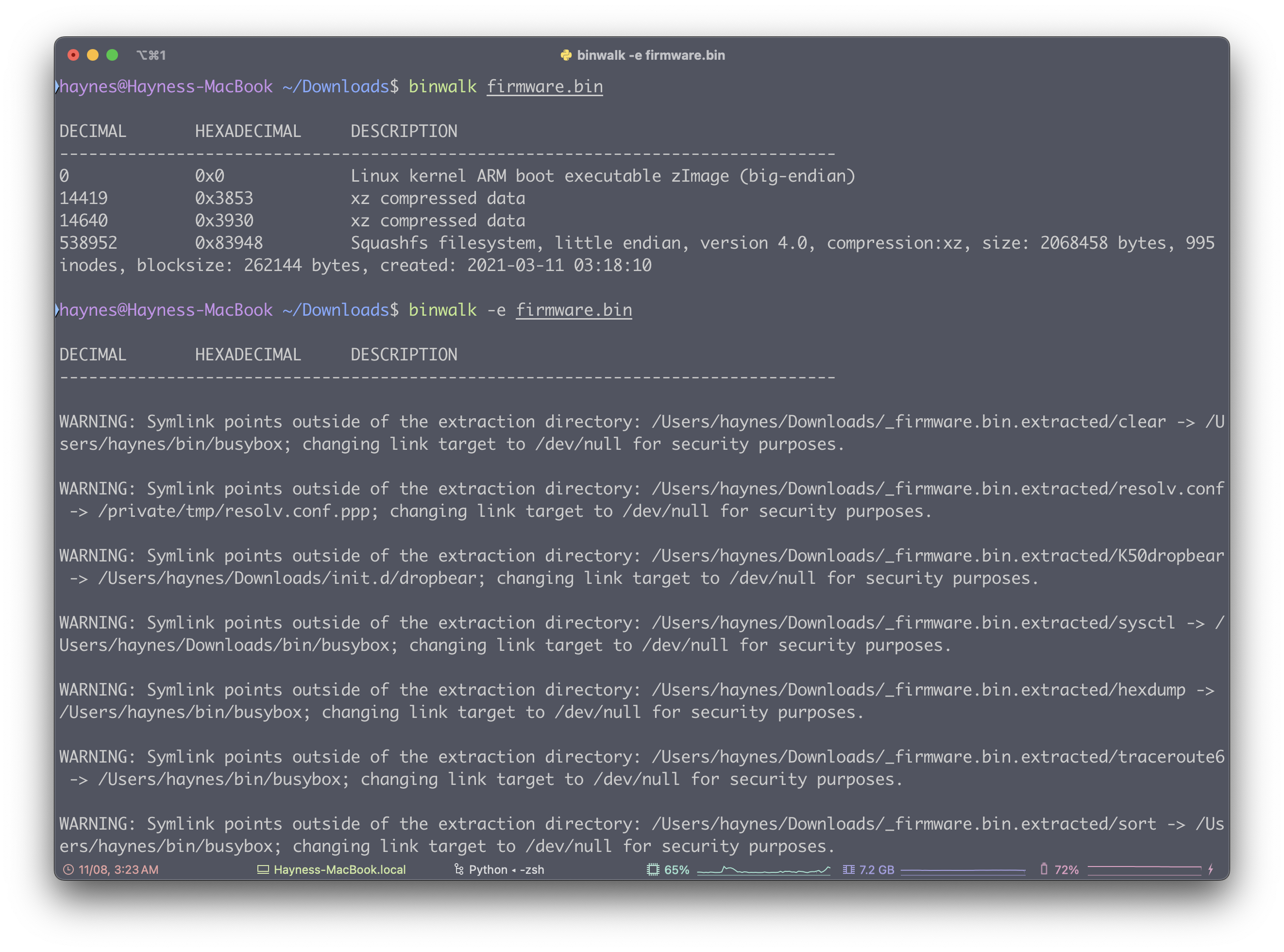
使用 nc 连接给的机子,发现需要登录一个 shell 才能进入,所以我们需要在固件中寻找用户名和密码
使用 grep 命令查找 login 关键字
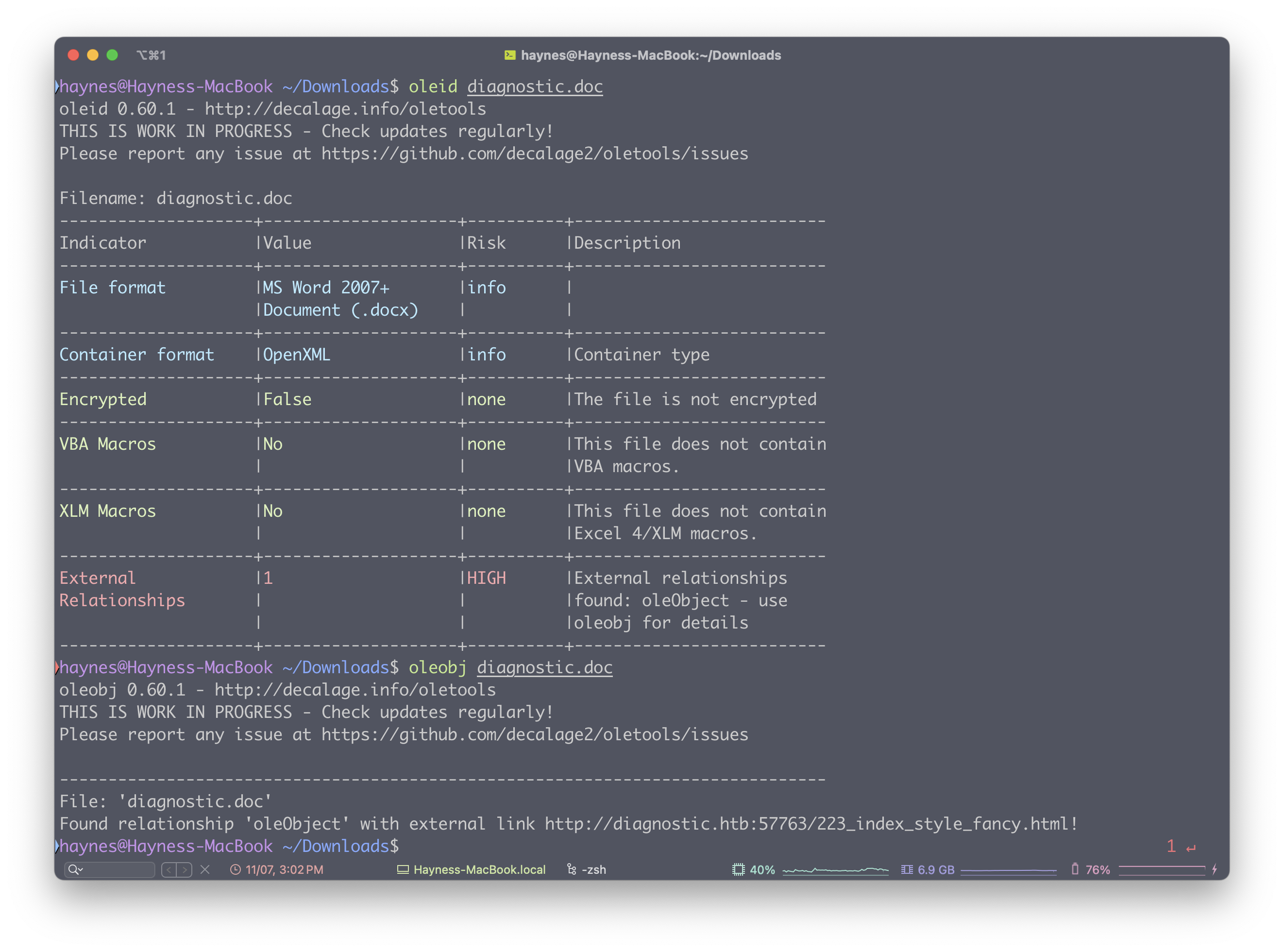
Our SOC has identified numerous phishing emails coming in claiming to have a document about an upcoming round of layoffs in the company. The emails all contain a link to diagnostic.htb/layoffs.doc. The DNS for that domain has since stopped resolving, but the server is still hosting the malicious document (your docker). Take a look and figure out what's going on.