
Hack the box Writeup CTF Planning
2025年9月2日...大约 5 分钟

胆小鬼连幸福都害怕,碰到棉
——「人间失格」


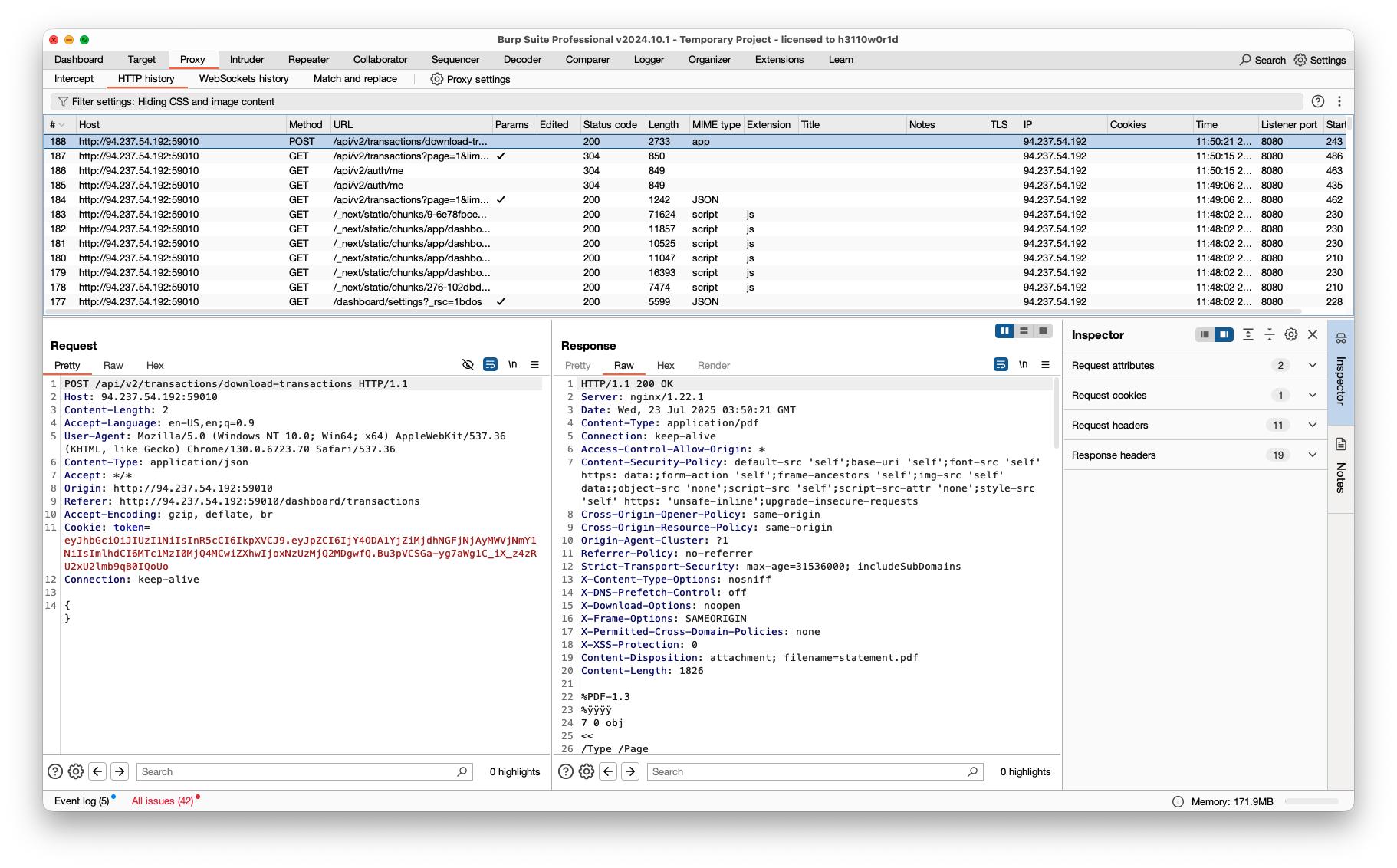
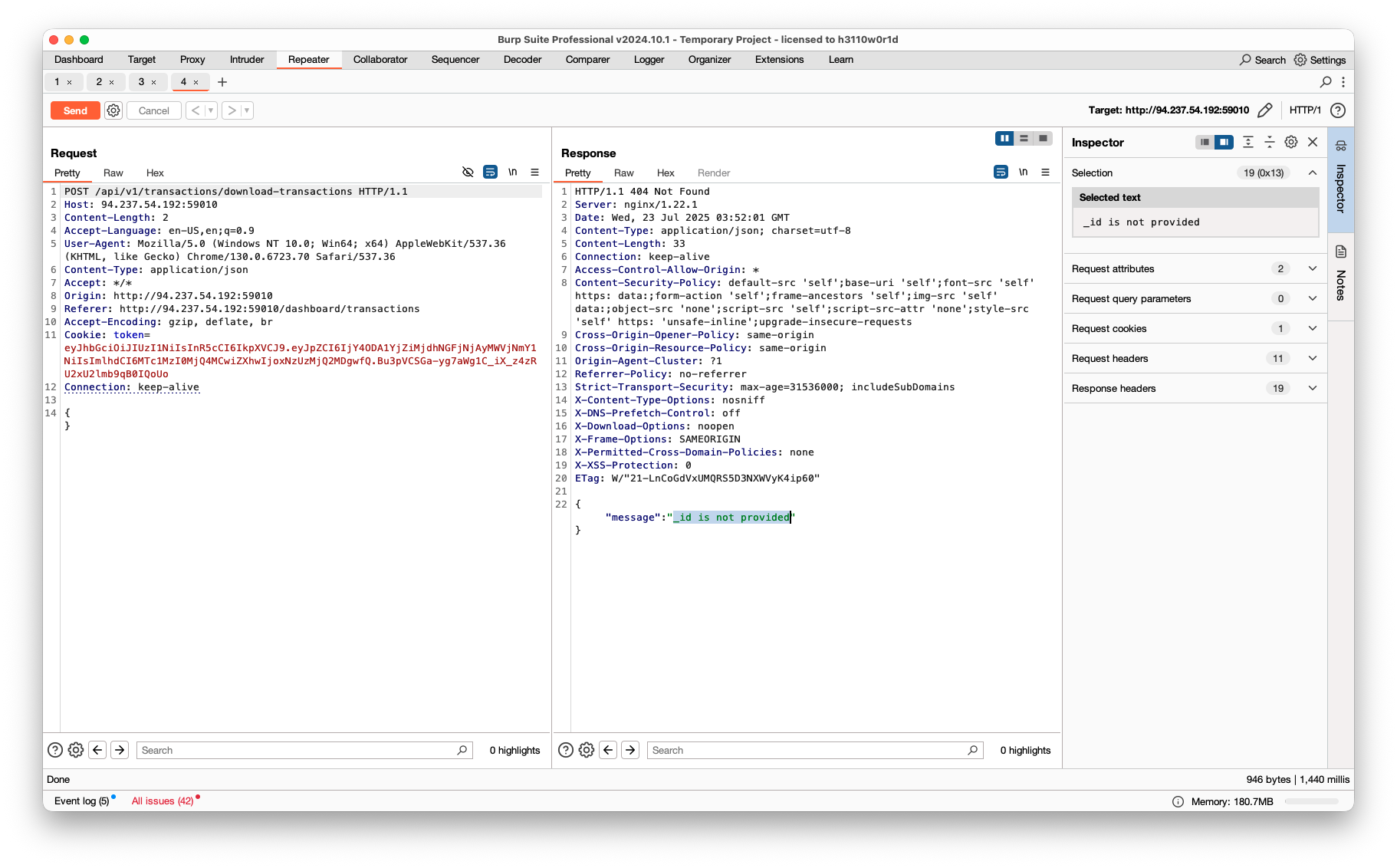
在数据包中可以看到所有的请求接口都是 v2 版本的,尝试使用 v1 版本的接口。
在下载交易PDF的接口时,使用 v1 版本的接口发现不需要使用JWT鉴权,而是使用 _id 作为参数。


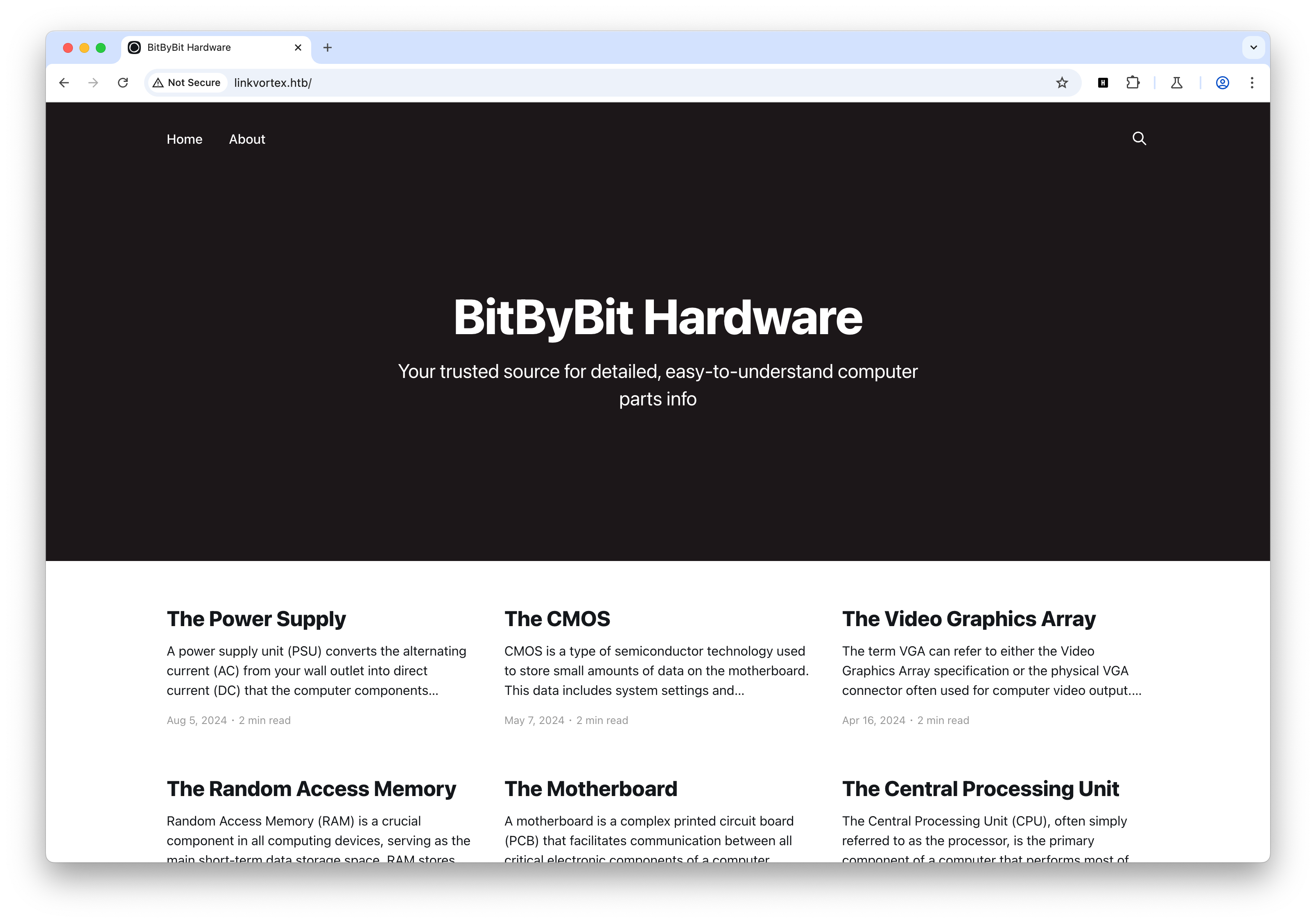
dev.linkvortex.htb)$ rustscan -a 10.10.11.47
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.47:22
Open 10.10.11.47:80
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} -{{ipversion}} {{ip}} -Pn -sV -A" on ip 10.10.11.47
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-18 17:56 HKT
Scanning dev.linkvortex.htb (10.10.11.47) [2 ports]
Discovered open port 22/tcp on 10.10.11.47
Discovered open port 80/tcp on 10.10.11.47
Nmap scan report for dev.linkvortex.htb (10.10.11.47)
Host is up, received user-set (0.29s latency).
Scanned at 2025-03-18 17:56:17 HKT for 9s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:f8:b9:68:c8:eb:57:0f:cb:0b:47:b9:86:50:83:eb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMHm4UQPajtDjitK8Adg02NRYua67JghmS5m3E+yMq2gwZZJQ/3sIDezw2DVl9trh0gUedrzkqAAG1IMi17G/HA=
| 256 a2:ea:6e:e1:b6:d7:e7:c5:86:69:ce:ba:05:9e:38:13 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKKLjX3ghPjmmBL2iV1RCQV9QELEU+NF06nbXTqqj4dz
80/tcp open http syn-ack Apache httpd
| http-git:
| 10.10.11.47:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
|_ https://github.com/TryGhost/Ghost.git
|_http-title: Launching Soon
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel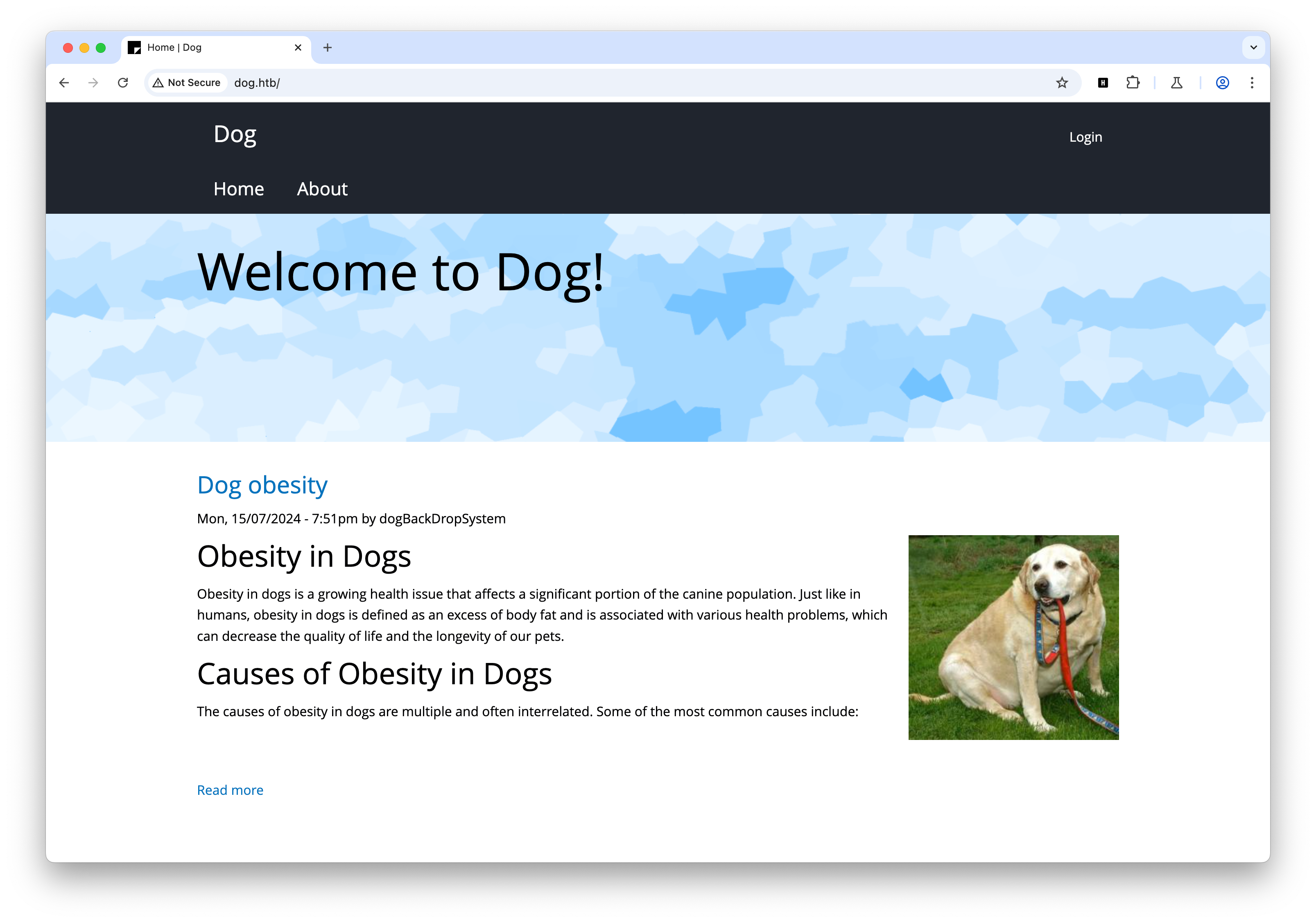
dog.htb)$ rustscan -a 10.10.11.58 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/Users/haynes/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.58:22
Open 10.10.11.58:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-11 16:17 CST
Initiating Ping Scan at 16:17
Scanning 10.10.11.58 [2 ports]
Completed Ping Scan at 16:17, 0.44s elapsed (1 total hosts)
Initiating Connect Scan at 16:17
Scanning dog.htb (10.10.11.58) [2 ports]
Discovered open port 22/tcp on 10.10.11.58
Discovered open port 80/tcp on 10.10.11.58
Completed Connect Scan at 16:17, 0.44s elapsed (2 total ports)
Nmap scan report for dog.htb (10.10.11.58)
Host is up, received syn-ack (0.42s latency).
Scanned at 2025-03-11 16:17:12 CST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /opt/homebrew/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.91 seconds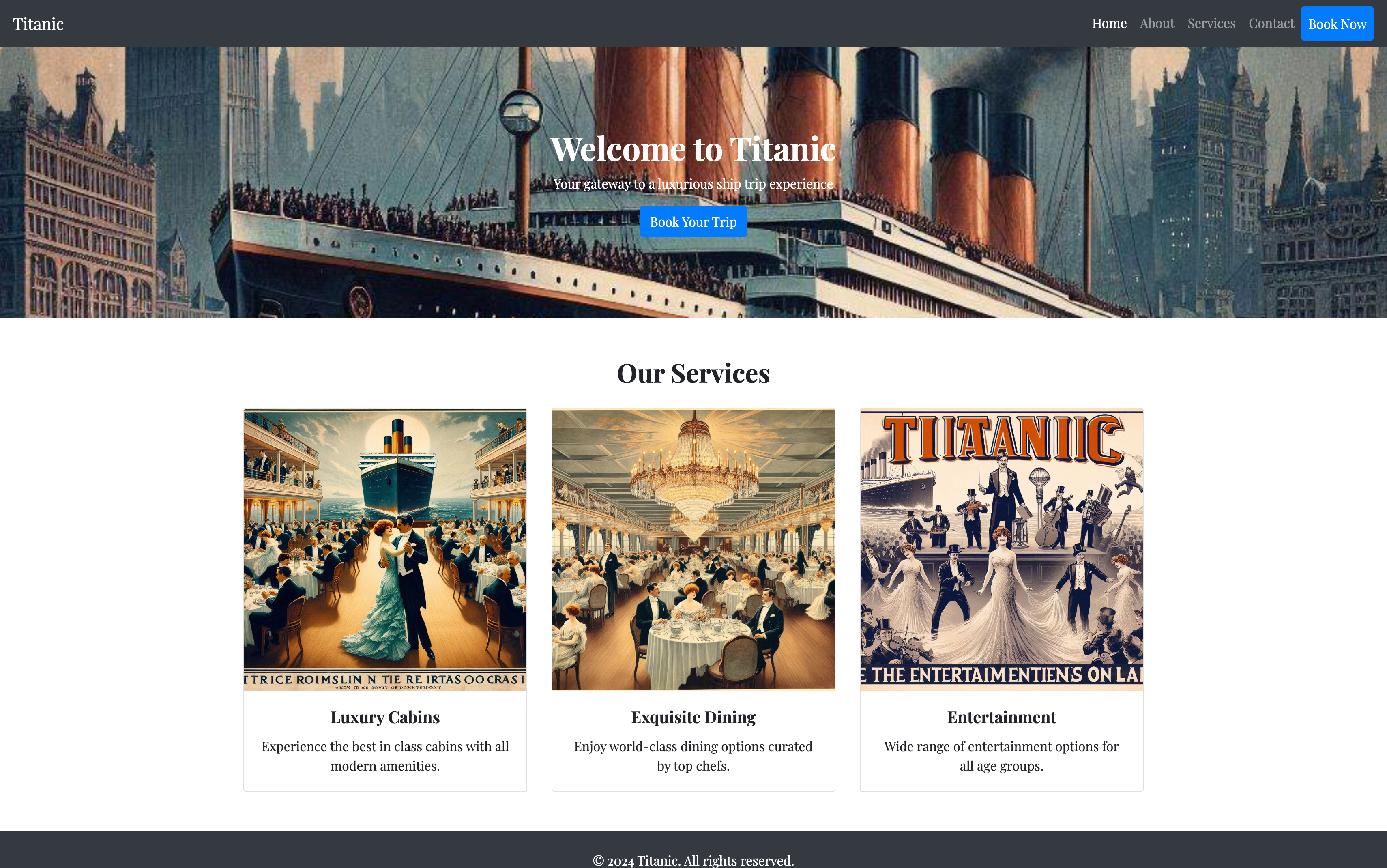
用 rustscan 扫描靶机端口
$ rustscan -a 10.10.11.55 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Making sure 'closed' isn't just a state of mind.
[~] The config file is expected to be at "/Users/haynes/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.55:22
Open 10.10.11.55:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-10 16:55 CST
Initiating Ping Scan at 16:55
Scanning 10.10.11.55 [2 ports]
Completed Ping Scan at 16:55, 0.76s elapsed (1 total hosts)
Initiating Connect Scan at 16:55
Scanning titanic.htb (10.10.11.55) [2 ports]
Discovered open port 80/tcp on 10.10.11.55
Discovered open port 22/tcp on 10.10.11.55
Completed Connect Scan at 16:55, 0.47s elapsed (2 total ports)
Nmap scan report for titanic.htb (10.10.11.55)
Host is up, received conn-refused (0.37s latency).
Scanned at 2025-03-10 16:55:04 CST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack